Introduction:
Hello bug hunters!!! Have you ever found a bug in 20 mins? maybe of you might have achieved it, but generally finding a P4 level bug for a good rewarding platform isn’t easy, even if you find it you face a lot of Duplicates, and the patience required to find an extremely good vulnerability takes all blood, sweat and the most precious time. sometimes it annoys but today this article will not just tell you how to find a good shiny, very less known vulnerability by which you can even dodge duplicates, by exploiting that bug even more.
First things first! what’s a P4 bug?
As I’m writing this Article keeping the beginners in mind, so it’s important to explain with the basic to clear each and every problem which arises in their mind! usually we use these “P” series of denotations to explain the severity of the bug, in some bug bounty platforms we can even see just a simple table, going from low to critical.
where this P4 bug may vary from low to medium which depends on the impact of that bug for the particular scope, so where does this “P” series come in limelight? so, it’s bugcrowd platform, which is one of the major, globally recognized bug management programs, which allows Security researchers to find bugs for their customers (which are generally Large MNC’s or Organizations who want to check for the bugs in their systems). so, what’s the “P” series all about: –
- P1 – Critical (Bounty varies from $1k-$5k, even more in some cases)
- P2 – High (up to $800)
- P3 – medium (up to $500)
- P4 – low (up to $200)
- P5 – Informational (mostly bounty is not paid for this)
note :- this is a general scale for bounty rewarded by programs, it may vary program to program.
To know more about Bugcrowd’s Vulnerability Rating Taxonomy (VRT), in easy word to know about what bug lies in which severity you may read this: – Bugcrowd’s Vulnerability Rating Taxonomy – Bugcrowd
The easiest bug: Metadata not stripped from images!!!
If you don’t know, or even if you know, sometime when you click photos from your phone, it saves some of the data, for example date, time, camera name, camera setting and many more device settings like camera and picture details, which isn’t really is a concern. But main role for this vulnerability comes from Location. your images sometime record the co-ordinates of your location which can easily tell where the photo is taken. sometimes it is so private that it can’t be shared to others. but is it all about the impact of this P4 bug? well no!!!
Impact of this bug(technically): –
As we’ve discussed about the impact of this P4 bug on one’s privacy, but it is not all about this bug. if any web application or software is not stripping this data an attacker can even perform XSS (cross site scripting) attack or even it can let any attacker perform RCE (Remote Code execution), well! you might be wondering how is this possible with this kind of easy P4 bug? but yes! don’t worry I’ll share some articles which will make you believe so.
How to find this bug: –
So, it’s really easy, here are the steps: –
- go to any website/scope.
- register or log in
- go to profile
- see for the profile picture option
- exif-samples/jpg at master · ianare/exif-samples · GitHub – download any image from here containing location data.
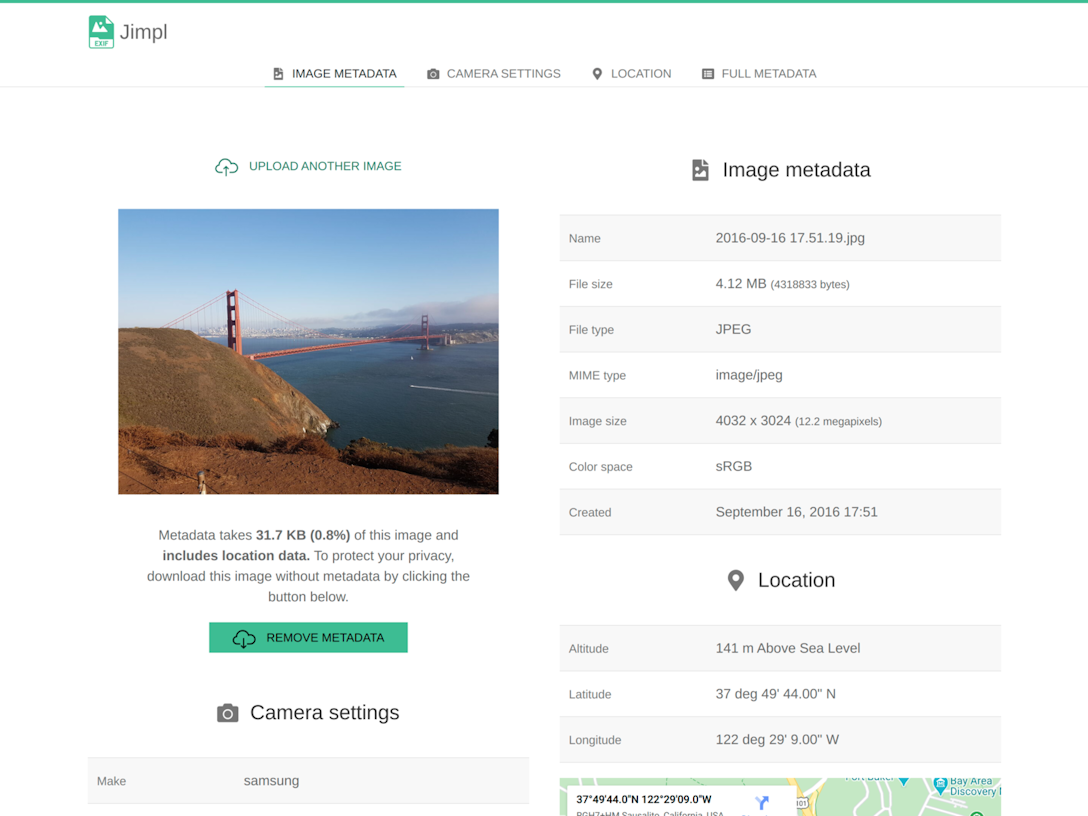
- go to jimpl or any tool like exiftool, test your image if it has geo location and other metadata.
- Now upload this image into the profile picture.
- after the image is uploaded, do right click and download it from there.
- put the downloaded image into the jimpl, and check for same metadata (Location is compulsory).
- Hurray!!! you have find the bug.
disclosed Hackerone report for reference of this bug: –
Reddit | Report #1069039 – GPS metadata preserved when converting HEIF to PNG | HackerOne
Note: – there are chances of this bug getting Duplicated, but don’t worry here’s how you can update this P4 into P3 or even more severe: –
How to upgrade the severity of this P4 bug by exploiting it: –
here are some articles you may prefer: –
For XSS: –
For RCE: – (Highly recommended)
Remote Code Execution via Exif Data- I’m Dangerous | by Jerry Shah (Jerry) | Medium
Happy Hacking 😉
Thank you for reading till last😊, hope you got to learn something from this, for getting more article similar to this topic you can stay tuned. If you’re interested in knowing more about such topics you can read about AI Taking Jobs!!!