Introduction
The Common Vulnerability Scoring System (CVSS) is an open framework designed to provide a consistent method for measuring the severity of software vulnerabilities. Developed by the Forum of Incident Response and Security Teams (FIRST), CVSS is widely used by security professionals, software vendors, and organizations to assess and prioritize vulnerabilities. This article will provide a detailed, step-by-step guide on how to calculate a CVSS score, covering its components, metrics, and the scoring process.
To calculate CVSS Score you can navigate to official NIST website: NVD – CVSS v3 Calculator (nist.gov)
Understanding CVSS
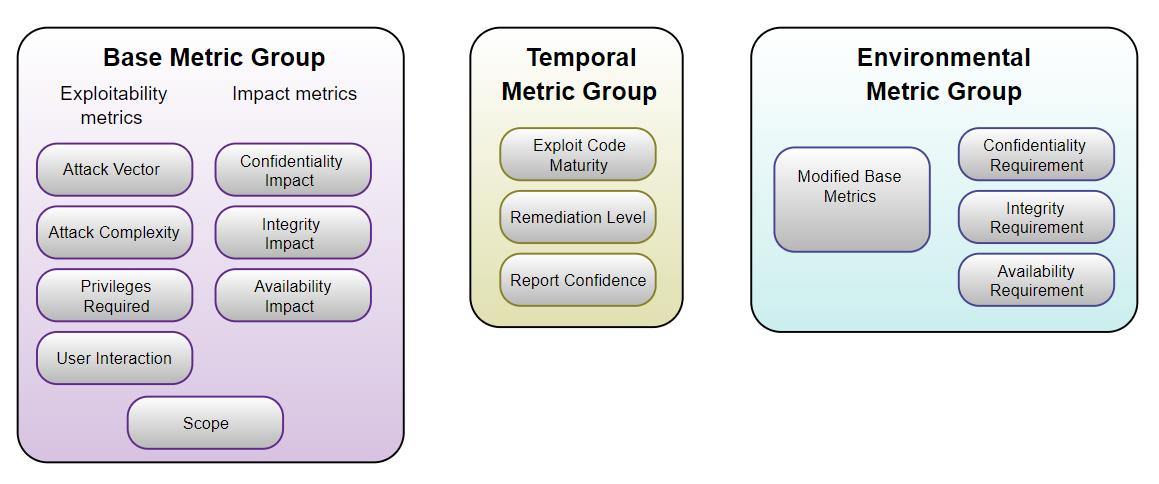
CVSS is composed of three metric groups:
- Base Metrics: These represent the intrinsic characteristics of a vulnerability and are constant over time and user environments.
- Temporal Metrics: These represent characteristics that change over time, such as the availability of a fix.
- Environmental Metrics: These represent the characteristics of a vulnerability that are specific to a user’s environment.
Each metric group consists of various metrics that are used to calculate a numerical score, which in turn helps in understanding the severity of the vulnerability.
Base Metrics
The Base Metrics group consists of several components, each of which contributes to the overall CVSS Base Score. The Base Score is the starting point for the CVSS score and is designed to be as objective and consistent as possible.
1. Attack Vector (AV)

The Attack Vector metric describes how a vulnerability is exploited. It has four possible values:
- Network (N): The vulnerability can be exploited remotely over a network.
- Adjacent Network (A): The vulnerability requires an attacker to be on the same local network.
- Local (L): The attacker needs physical or local access to the vulnerable system.
- Physical (P): The attacker needs physical interaction with the affected system.
Impact on CVSS Score: A vulnerability that can be exploited remotely (Network) generally receives a higher score than one that requires local access.
2. Attack Complexity (AC)

The Attack Complexity metric assesses the conditions required to exploit the vulnerability. It has two possible values:
- Low (L): Exploitation is straightforward and does not require specialized conditions.
- High (H): Exploitation requires specific conditions or is more complex.
Impact on CVSS Score: Vulnerabilities that are easier to exploit (Low) have a higher score compared to those requiring complex conditions.
3. Privileges Required (PR)
This metric describes the level of privileges an attacker needs to exploit the vulnerability. It has three possible values:
- None (N): No privileges are required.
- Low (L): Low-level privileges are required.
- High (H): High-level privileges are required.
Impact on CVSS Score: Vulnerabilities that can be exploited with no privileges (None) typically receive a higher score.
4. User Interaction (UI)
The User Interaction metric assesses whether the exploitation of the vulnerability requires user involvement. It has two possible values:
- None (N): No user interaction is required.
- Required (R): User interaction is required.
Impact on CVSS Score: Vulnerabilities that do not require user interaction (None) usually have a higher score compared to those that do.
5. Scope (S)
The Scope metric describes whether the exploitation of the vulnerability impacts only the vulnerable component or if it affects other components as well. It has two possible values:
- Unchanged (U): The exploitation affects only the vulnerable component.
- Changed (C): The exploitation impacts additional components beyond the vulnerable one.
Impact on CVSS Score: Vulnerabilities that affect additional components (Changed) have a higher score.
6. Confidentiality Impact (C)
This metric measures the impact on the confidentiality of the information. It has three possible values:
- None (N): No impact on confidentiality.
- Low (L): Confidential information is partially exposed.
- High (H): Confidential information is completely exposed.
Impact on CVSS Score: Higher impacts on confidentiality (High) lead to a higher score.
7. Integrity Impact (I)
The Integrity Impact metric assesses the impact on the integrity of the information. It has three possible values:
- None (N): No impact on integrity.
- Low (L): Integrity is partially affected.
- High (H): Integrity is fully compromised.
Impact on CVSS Score: Higher impacts on integrity (High) lead to a higher score.
8. Availability Impact (A)
This metric describes the impact on the availability of the system. It has three possible values:
- None (N): No impact on availability.
- Low (L): Availability is partially affected.
- High (H): Availability is fully impacted.
Impact on CVSS Score: Vulnerabilities with higher impacts on availability (High) have a higher score.
Temporal Metrics
Temporal Metrics reflect the characteristics of a vulnerability that change over time, such as the availability of a fix or the existence of exploit code. These metrics are optional and can modify the Base Score.
1. Exploit Code Maturity (E)

This metric assesses the availability and quality of exploit code for the vulnerability. It has four possible values:
- Not Defined (X): Not applicable.
- Unproven (U): No exploit code is available.
- Proof-of-Concept (P): Exploit code is available but not fully functional.
- Functional (F): Exploit code is reliable and functional.
- High (H): Exploit code is widely available and fully functional.
Impact on CVSS Score: A higher maturity of exploit code (Functional, High) generally increases the score.
2. Remediation Level (RL)

This metric measures the availability of a fix or patch for the vulnerability. It has four possible values:
- Not Defined (X): Not applicable.
- Official Fix (O): An official fix or patch is available.
- Temporary Fix (T): A temporary solution is available but may not be permanent.
- Workaround (W): Workarounds are available but may not fully mitigate the vulnerability.
- Unavailable (U): No fix or workaround is available.
Impact on CVSS Score: Vulnerabilities with no available fix or workaround (Unavailable) typically have a higher score.
3. Report Confidence (RC)
This metric assesses the reliability of the information regarding the vulnerability. It has three possible values:
- Not Defined (X): Not applicable.
- Unknown (U): The vulnerability details are not well-known.
- Reasonable (R): The vulnerability details are reasonably well-known.
- Confirmed (C): The vulnerability details are confirmed and well-documented.
Impact on CVSS Score: Higher confidence in the report (Confirmed) may not directly impact the Base Score but affects the Temporal Score.
Environmental Metrics
Environmental Metrics account for the specific context of the vulnerability within an organization’s environment. These metrics are optional and allow for customization of the CVSS score based on the environment in which the vulnerability is assessed.
1. Modified Attack Vector (MAV)
The Modified Attack Vector metric assesses if the attack vector changes based on the specific environment. It has the same values as the Attack Vector metric.
2. Modified Attack Complexity (MAC)
The Modified Attack Complexity metric assesses if the complexity of the attack changes based on the specific environment. It has the same values as the Attack Complexity metric.
3. Modified Privileges Required (MPR)
The Modified Privileges Required metric assesses if the level of privileges required changes based on the specific environment. It has the same values as the Privileges Required metric.
4. Modified User Interaction (MUI)
The Modified User Interaction metric assesses if user interaction requirements change based on the specific environment. It has the same values as the User Interaction metric.
5. Modified Scope (MS)
The Modified Scope metric assesses if the impact of the vulnerability changes based on the specific environment. It has the same values as the Scope metric.
6. Modified Confidentiality Impact (MC)
The Modified Confidentiality Impact metric assesses if the confidentiality impact changes based on the specific environment. It has the same values as the Confidentiality Impact metric.
7. Modified Integrity Impact (MI)
The Modified Integrity Impact metric assesses if the integrity impact changes based on the specific environment. It has the same values as the Integrity Impact metric.
8. Modified Availability Impact (MA)
The Modified Availability Impact metric assesses if the availability impact changes based on the specific environment. It has the same values as the Availability Impact metric.
Calculating the CVSS Score
Step 1: Determine Base Metrics
First, gather all the necessary information to assess the Base Metrics:
- Attack Vector (AV)
- Attack Complexity (AC)
- Privileges Required (PR)
- User Interaction (UI)
- Scope (S)
- Confidentiality Impact (C)
- Integrity Impact (I)
- Availability Impact (A)
Step 2: Calculate the Base Score
The Base Score is calculated using the following formula:
Where:
- Impact Subscore is derived from the Confidentiality Impact, Integrity Impact, and Availability Impact metrics.
- Exploitability Subscore is derived from the Attack Vector, Attack Complexity, Privileges Required, and User Interaction metrics.
The specific formulas and calculations are defined in the CVSS v3.1 specification.
Step 3: Determine Temporal Metrics
Assess the Temporal Metrics:
Step 4: Calculate the Temporal Score
The Temporal Score is calculated by adjusting the Base Score based on the values of the Temporal Metrics. The formula for the Temporal Score is:
Temporal Score=roundup(Base Score×Exploit Code Maturity×Remediation Level×Report Confidence)
Step 5: Determine Environmental Metrics
Assess the Environmental Metrics:
- Modified Attack Vector (MAV)
- Modified Attack Complexity (MAC)
- Modified Privileges Required (MPR)
- Modified User Interaction (MUI)
- Modified Scope (MS)
- Modified Confidentiality Impact (MC)
- Modified Integrity Impact (MI)
- Modified Availability Impact (MA)
Step 6: Calculate the Environmental Score
The Environmental Score is calculated by adjusting the Temporal Score based on the values of the Environmental Metrics. The formula for the Environmental Score is:








