Setting up a structured cybersecurity homelab is essential for practicing offensive (Red Team) and defensive (Blue Team) techniques. This guide covers how to design both Red Team and Blue Team environments, configure monitoring tools like Wazuh and ELK Stack, and deploy vulnerable environments such as Metasploitable 2/3, DVWA, and bWAPP.
Part 1: Red Team Lab Setup
A Red Team lab focuses on offensive security, allowing you to simulate hacking activities like network penetration, privilege escalation, and post-exploitation.
1.1 Virtualization Tools
Start by choosing a virtualization platform. Common options include:
- VirtualBox: Free and open-source, with straightforward networking configurations.
- VMware Workstation: Commercial-grade, ideal for advanced setups.
- Proxmox: Offers both virtualization and containers, excellent for complex setups.
1.2 Operating Systems
- Kali Linux: The go-to OS for penetration testing. Kali comes preinstalled with tools like Metasploit, Nmap, and Wireshark. Here’s how to install it on a VM:
sudo apt update && sudo apt full-upgrade -y
sudo apt install virtualbox-guest-x11
- Metasploitable 2: A purposefully vulnerable Linux machine, ideal for practicing exploits. You can import it into VirtualBox or VMware.
- Metasploitable 3: A more advanced version with both Windows and Linux targets. Follow the GitHub setup guide:
git clone https://github.com/rapid7/metasploitable3.git
cd metasploitable3
./build.sh
1.3 Other Vulnerable VMs
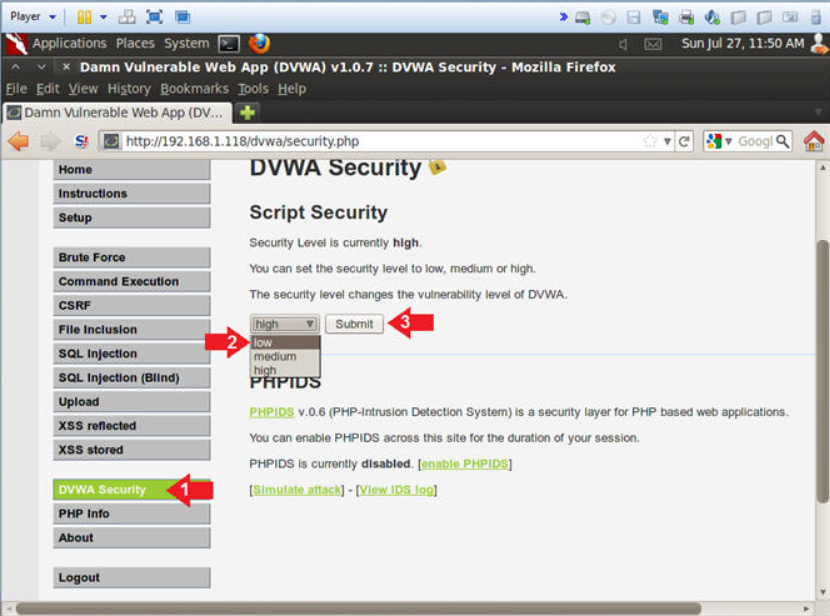
- Damn Vulnerable Web Application (DVWA): A PHP-based web app with intentional vulnerabilities for practicing SQL Injection, XSS, and more.
git clone https://github.com/digininja/DVWA.git
sudo apt install apache2 mysql-server php php-mysqli
sudo cp -r DVWA /var/www/html/
sudo service apache2 restart
- bWAPP: Another intentionally vulnerable web app for practicing a wide range of exploits.
wget https://sourceforge.net/projects/bwapp/files/latest/download
unzip bWAPP_latest.zip -d /var/www/html/bWAPP/
sudo service apache2 restart
Part 2: Blue Team Lab Setup
A Blue Team lab emphasizes defense, monitoring, and incident response. You’ll create an environment for log analysis, detection, and response to simulated attacks.
2.1 Operating Systems
For defensive operations, you’ll need to monitor both Windows and Linux machines:
- Windows Server: Simulate an enterprise Active Directory (AD) environment to detect lateral movement and privilege escalation.
- Ubuntu Server: Hosts services like web servers, databases, and network shares to simulate real-world attacks on production environments.
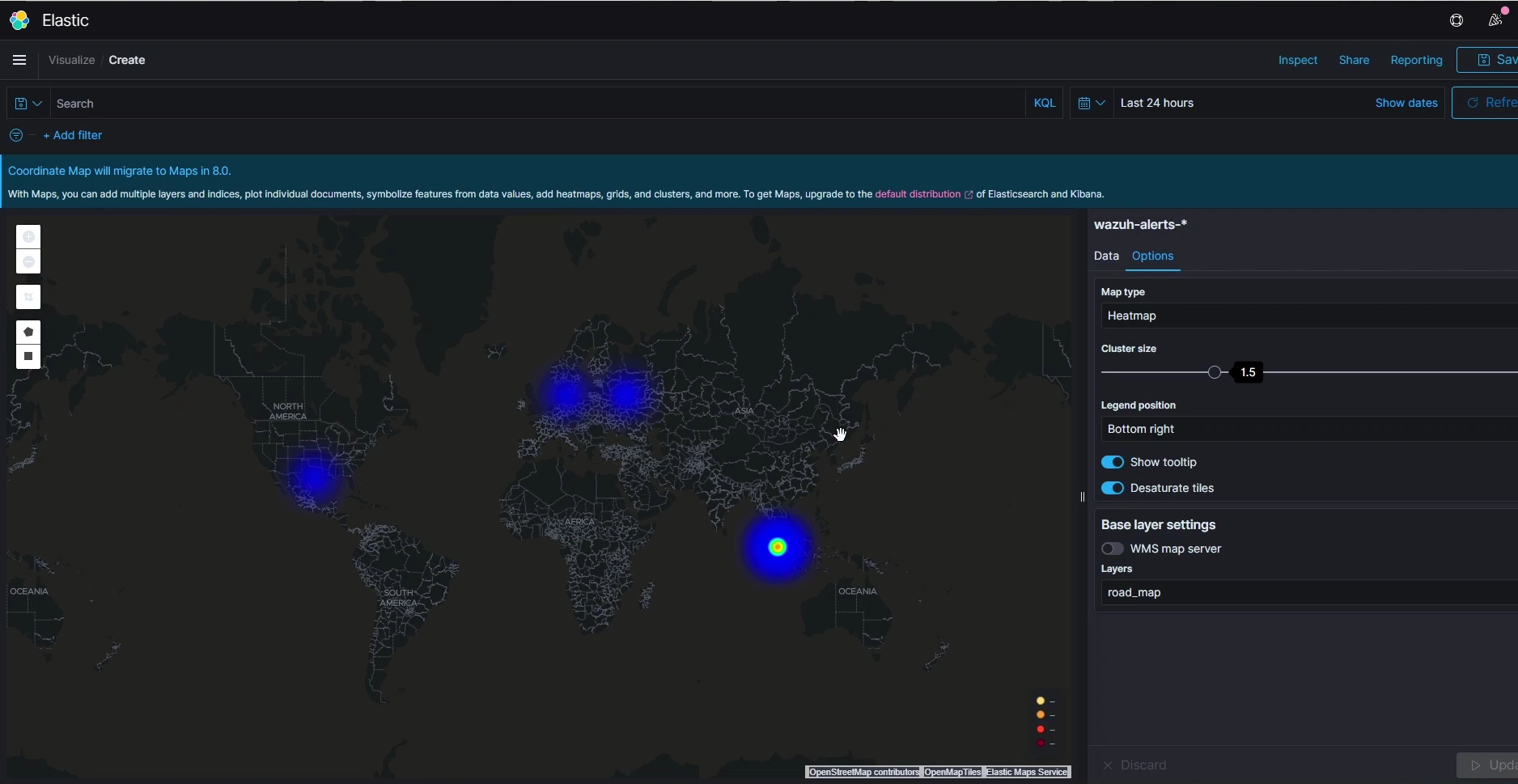
2.2 Wazuh: Open Source SIEM
Wazuh provides real-time monitoring and alerts, making it a must-have for your Blue Team lab. Here’s how to install it:
- Install Wazuh Manager on Ubuntu:curl -s https://packages.wazuh.com/key/GPG-KEY-WAZUH | sudo apt-key add –echo “deb https://packages.wazuh.com/4.x/apt stable main” | sudo tee /etc/apt/sources.list.d/wazuh.list
sudo apt update
sudo apt install wazuh-manager - Install agents on your target machines to capture logs and alerts. You can monitor both Linux and Windows environments for real-time alerts.
2.3 Network Monitoring
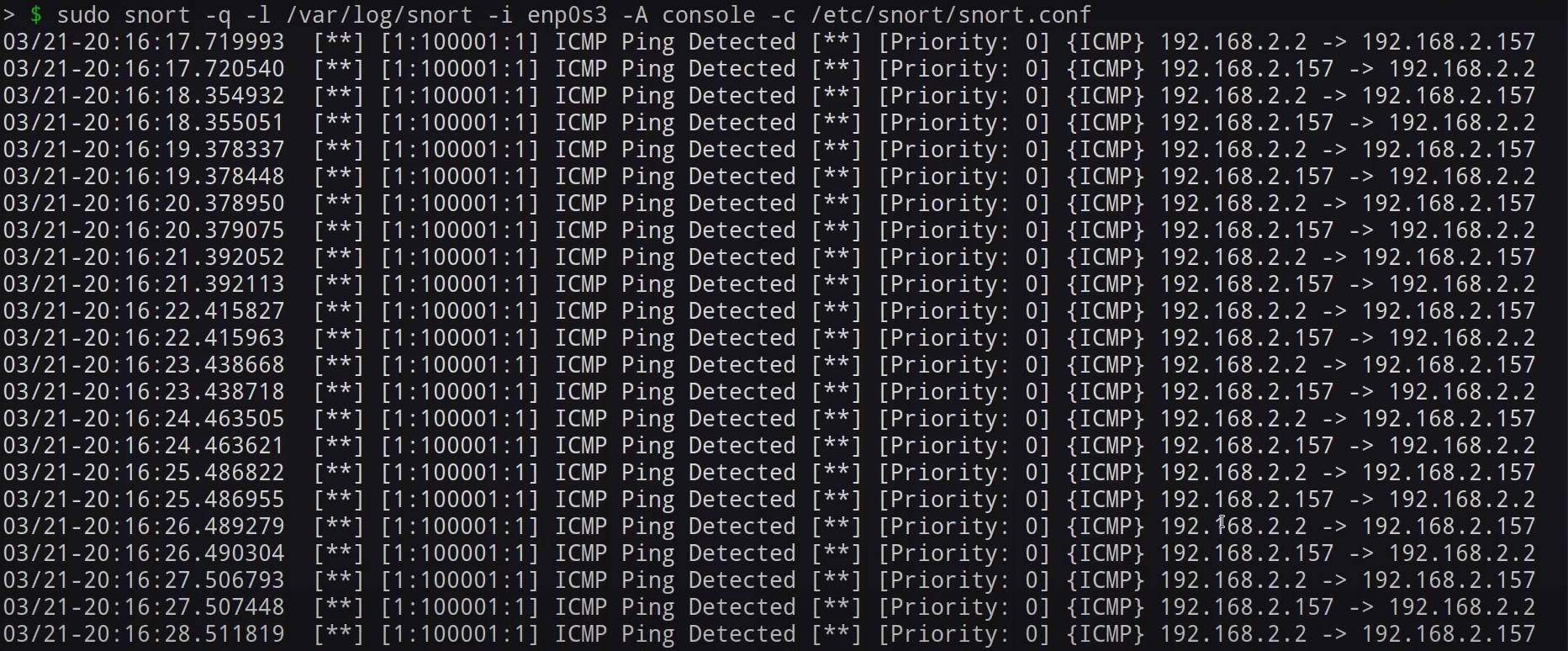
- Snort: An open-source intrusion detection system (IDS) that analyzes network traffic. Install Snort on Ubuntu:
sudo apt install snort
snort -A console -i eth0 -c /etc/snort/snort.conf
- Suricata: A powerful, modern IDS that is also suitable for intrusion prevention.
Part 3: Monitoring with the ELK Stack
The ELK Stack (Elasticsearch, Logstash, Kibana) is a widely-used log aggregation and visualization platform. It pairs well with Wazuh for centralized monitoring and detection.
3.1 Setting Up ELK Stack
- Elasticsearch:
sudo apt install elasticsearch
sudo systemctl start elasticsearch
sudo systemctl enable elasticsearch
- Logstash:
sudo apt install logstash
sudo systemctl start logstash
- Kibana:
sudo apt install kibana
sudo systemctl start kibana
3.2 Integrating Wazuh with ELK
Install the Wazuh plugin for Kibana:
sudo /usr/share/kibana/bin/kibana-plugin install https://packages.wazuh.com/4.x/kibana/wazuh-kibana-plugin-x.x.x_amd64.deb
Once installed, access Kibana at http://localhost:5601 to view dashboards and analyze security events from Wazuh.
Part 4: Vulnerable Applications for Hands-On Practice
In addition to Metasploitable and DVWA, several other platforms offer opportunities to practice your offensive and defensive skills.
4.1 OWASP Juice Shop
OWASP Juice Shop is a modern, intentionally vulnerable web application. To install it via Docker:
docker pull bkimminich/juice-shop
docker run –rm -p 3000:3000 bkimminich/juice-shop
4.2 Hack The Box (HTB)
Hack The Box provides virtual machines designed for Capture The Flag (CTF) style challenges. You can practice network penetration and root access exploits on HTB machines. Simply download the HTB OpenVPN file, connect, and start hacking.
Part 5: Other Essential Tools and Resources
- pfSense: A widely-used, open-source firewall solution for managing and securing network traffic. Set it up as a VM or on dedicated hardware.
- OpenVPN: Enables secure remote access to your lab, allowing you to simulate external penetration testing.
- Ansible: Automate your homelab by using Ansible to deploy multiple VMs and services.
- Bash Scripting: Automate tasks like network scanning or vulnerability checks using Bash. Example script to scan multiple hosts for open ports:
for ip in $(cat iplist.txt); do
echo “Scanning $ip”
nmap -p- $ip
done
Conclusion
A well-built homelab for Red and Blue Team activities offers a hands-on environment for mastering cybersecurity skills. With the right tools like Kali Linux, Metasploitable, Wazuh, and the ELK Stack, you can simulate real-world attacks and build defensive strategies. As you expand your lab, consider incorporating CTF challenges or complex malware analysis setups to continuously improve your skill set.