The advent of quantum computing has sparked a whirlwind of discussion across industries, especially within fields like cryptography and blockchain technology. Bitcoin—the world’s first decentralized cryptocurrency—has been at the forefront of this conversation due to its reliance on cryptographic techniques for security. Many wonder whether the emergence of quantum computing will eventually render Bitcoin’s cryptography obsolete and thus “break” the cryptocurrency.
In this article, we will explore the fundamentals of quantum computing, examine Bitcoin’s reliance on cryptographic algorithms, and analyze the potential threat quantum computing may pose to the cryptocurrency. We’ll also discuss possible solutions and mitigation strategies to safeguard Bitcoin against quantum-based attacks.
Understanding Quantum Computing
Before we dive into its potential effects on Bitcoin, it’s essential to understand the basics of quantum computing and how it differs from classical computing.
1.1. Classical vs. Quantum Computers
Traditional computers rely on bits, which are binary units of data represented as either 0s or 1s. Classical computing operates on a deterministic framework, where computations are performed in sequential steps using logical gates. While classical computers have made great strides in performance and processing speed, their ability to solve certain types of problems, particularly those involving large datasets and complex variables, is limited.
Quantum computers use quantum bits or qubits. Unlike classical bits, qubits can exist in multiple states simultaneously due to a property known as superposition. Additionally, qubits exhibit entanglement, where the state of one qubit is directly correlated with the state of another, regardless of the distance between them. These two principles—superposition and entanglement—allow quantum computers to perform calculations exponentially faster than classical computers.
1.2. Quantum Supremacy
Quantum supremacy refers to the point where a quantum computer can outperform the best classical computers for specific tasks. In 2019, Google claimed to have achieved quantum supremacy, though its practical impact was limited to specialized calculations. Nonetheless, this development indicates that quantum computing is no longer purely theoretical and is progressing toward real-world applications.
While we are still years away from large-scale, fully functional quantum computers, their potential capabilities have sparked concerns about their impact on security protocols, particularly in cryptography.
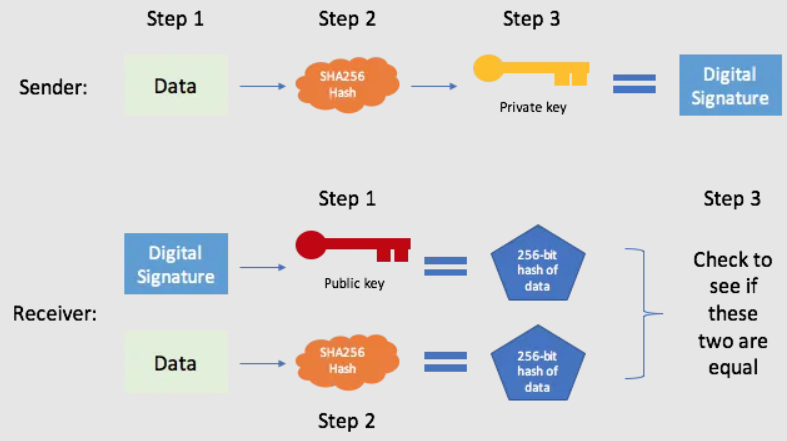
Bitcoin’s Cryptographic Foundation
Bitcoin is based on blockchain technology and relies heavily on cryptographic algorithms to ensure security, privacy, and immutability of transactions. There are two main cryptographic elements in Bitcoin’s design that could be vulnerable to quantum computing:
- Public-key Cryptography (Elliptic Curve Digital Signature Algorithm or ECDSA)
- Hashing Algorithms (SHA-256)
2.1. Elliptic Curve Cryptography (ECC) and ECDSA
Bitcoin uses elliptic curve cryptography (ECC) to generate pairs of public and private keys. The security of ECC relies on the mathematical difficulty of solving the elliptic curve discrete logarithm problem (ECDLP). In simpler terms, it is currently computationally infeasible for classical computers to derive a private key from its corresponding public key within a reasonable time frame.
The ECDSA (Elliptic Curve Digital Signature Algorithm) is used in Bitcoin to sign transactions and prove ownership of a particular private key without revealing the private key itself. This ensures that only the rightful owner of a Bitcoin address can authorize transactions.
Number of Bitcoin Private Key
The number of possible Bitcoin private keys is astronomically large. Bitcoin private keys are 256-bit numbers, meaning there are 2^256 possible combinations. This results in approximately 1.1579 x 10^77 possible Bitcoin private keys, a number so vast that it dwarfs the total number of atoms in the observable universe. This immense space of possible keys makes it virtually impossible for a classical computer to brute-force search for a private key. However, the rise of quantum computers, as we will see, introduces a different level of threat to this seemingly insurmountable key space.

2.2. SHA-256 Hashing Algorithm
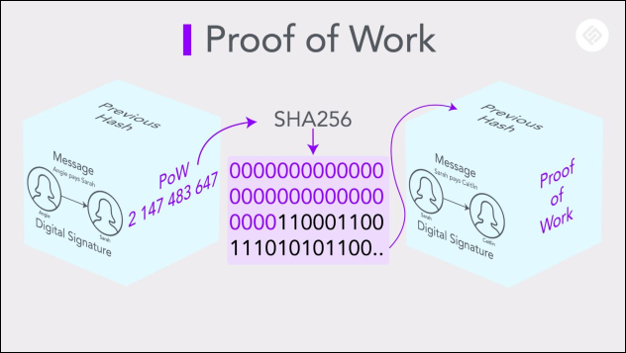
SHA-256 is a cryptographic hash function used in Bitcoin’s proof-of-work (PoW) consensus mechanism. Miners compete to solve cryptographic puzzles based on SHA-256, and the first one to find a solution can append a new block of transactions to the blockchain. The strength of SHA-256 lies in its resistance to preimage and collision attacks, meaning it’s extremely difficult to reverse-engineer the original input or find two different inputs that produce the same output.
Each SHA-256 hash calculation creates a 64-character hexadecimal number, which represents the hash value of the input. In Bitcoin’s mining process, miners must find a hash that meets specific criteria set by the network, making it difficult to predict or manipulate the outcome. This process currently secures the blockchain, but quantum computers could eventually challenge SHA-256’s strength.
Quantum Computing and Its Threat to Bitcoin
Quantum computing poses a threat to both the ECDSA and the SHA-256 hashing algorithm. The question is whether quantum computers will eventually become powerful enough to exploit the weaknesses in these cryptographic algorithms.
3.1. Breaking ECDSA with Shor’s Algorithm
One of the most well-known quantum algorithms is Shor’s algorithm, which can efficiently solve problems like integer factorization and discrete logarithms. This algorithm would allow a quantum computer to break the ECDSA used in Bitcoin by deriving a private key from a public key, something that would take classical computers an infeasible amount of time to accomplish.
Currently, it is estimated that a sufficiently powerful quantum computer with thousands or millions of qubits would be able to break Bitcoin’s ECDSA-based public key cryptography. In such a scenario, the security model of Bitcoin would collapse, as quantum attackers could forge signatures and spend bitcoins they do not own.
3.2. Quantum Attacks on SHA-256
While ECDSA is vulnerable to Shor’s algorithm, the situation for SHA-256 is slightly different. A quantum algorithm called Grover’s algorithm could potentially reduce the time required to perform a brute-force attack on a cryptographic hash function like SHA-256. In classical computing, finding a preimage requires 2^256 operations, but with Grover’s algorithm, a quantum computer could reduce this to roughly 2^128 operations.
Though this represents a significant reduction in complexity, 2^128 operations still represent an incredibly large number of computations, and it would require a quantum computer with a substantial number of qubits to perform this task efficiently. Therefore, the threat posed to Bitcoin’s PoW mechanism is less imminent than the threat to ECDSA, but it is still a concern in the long term.
Timeline: When Will Quantum Computers Pose a Real Threat?
The timeline for when quantum computers could realistically threaten Bitcoin is still uncertain. While progress is being made, large-scale quantum computers capable of running Shor’s algorithm effectively are likely years, if not decades, away.
Estimates vary, but many researchers believe that it could take at least 10-20 years before quantum computers with enough qubits and error-correction capabilities are available to threaten Bitcoin’s ECDSA or SHA-256 algorithms. Some conservative estimates push this timeline even further into the future.
However, given the rapid pace of innovation in the field of quantum computing, it would be unwise for the cryptocurrency community to ignore the threat. It’s crucial to begin preparing for a quantum-resistant future now, rather than waiting until quantum computing reaches maturity.
Possible Solutions and Mitigation Strategies
Fortunately, the threat posed by quantum computing is not insurmountable. The cryptographic community is actively researching and developing quantum-resistant algorithms and strategies that could protect Bitcoin from quantum-based attacks.
5.1. Post-Quantum Cryptography
Post-quantum cryptography refers to cryptographic algorithms that are resistant to both classical and quantum attacks. Several types of post-quantum cryptographic algorithms are being developed, including lattice-based, hash-based, and multivariate quadratic cryptography.
One potential solution for Bitcoin would be to replace the existing ECDSA algorithm with a quantum-resistant alternative. This would require a soft fork or hard fork of the Bitcoin network, but it could be implemented before quantum computers become a practical threat.
5.2. Strengthening Proof-of-Work
As quantum computers advance, Bitcoin’s proof-of-work (PoW) algorithm may need to be adjusted to account for Grover’s algorithm. One possible solution is to increase the difficulty of the PoW algorithm to ensure that even quantum computers would require significant computational resources to mine new blocks.
5.3. Quantum-Resistant Blockchains
Several blockchain projects, such as QANplatform and Quantum Resistant Ledger, are developing quantum-resistant blockchains from the ground up. While Bitcoin could theoretically implement quantum-resistant cryptography, these projects aim to build a quantum-safe foundation from the start.
Difference Between Quantum Cryptography and Quantum-Resistant Algorithms
Quantum Cryptography
Pros: Proven Security: Offers strong security that is theoretically secure against any future quantum computing advancements.
Cons: Infrastructure Requirements: Requires a dedicated point-to-point optical fiber network, making deployment complex and expensive.
Keying Challenges: Has strict key management and distribution requirements, necessitating secure key exchange for effective use.
Quantum-Resistant Algorithms
Pros: Ease of Integration: Can be more easily incorporated into existing IT systems and infrastructure without significant changes.
Cons: Unproven Security: While designed to be secure against quantum attacks, they have not yet been proven to be perfectly secure.
Vulnerability to Future Discoveries: May be susceptible to new quantum algorithms or discoveries that could undermine their security
Conclusion
Quantum computing is an exciting and revolutionary field with the potential to transform industries across the board. However, its potential to break current cryptographic systems is a significant concern for cryptocurrencies like Bitcoin. While Bitcoin’s reliance on ECDSA and SHA-256 is currently secure against classical computing attacks, the advent of quantum computing could present serious challenges in the future.
Fortunately, the cryptographic community is actively working on post-quantum algorithms and solutions that could mitigate these risks. By transitioning to quantum-resistant cryptography, increasing the difficulty of proof-of-work, and improving key management practices, Bitcoin can prepare for a post-quantum future and continue to serve as a secure, decentralized digital currency.