Active Directory ACL
When we talk about ACL-based attacks, we are specifically referring to Access Control Entries (ACEs) which populate Discretionary Access Control Lists (DACLs). DACLs reside within security descriptors, which reside within securable objects. Active Directory users, groups, and computers are securable objects. Access Control Entries describe the allowed and denied permissions for other principals in Active Directory against the securable object.
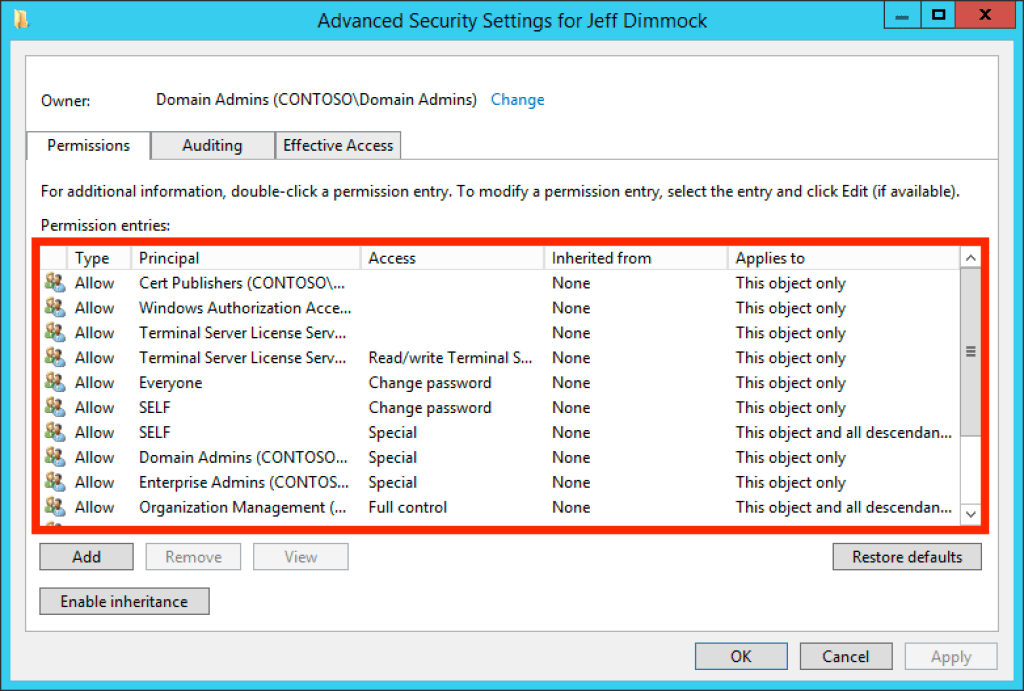
Above: The graphical representation of the security descriptor for the user “Jeff Dimmock”. Highlighted in red is the Discretionary Access Control List (DACL), comprised of Access Control Entries (ACEs).
The best example of this is when one object has “full control” over another object. Consider the “Domain Admins” group, for example. It makes sense that the “Domain Admins” group would have full control over every other object in a domain:
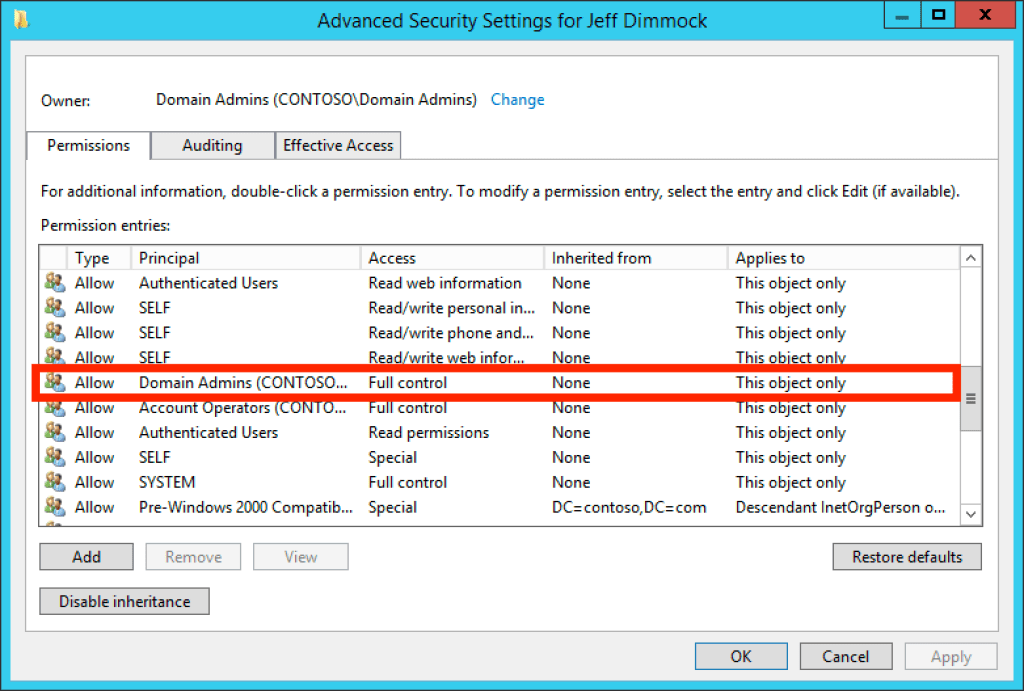
Above: The ACE granting the “Domain Admins” group full control of the “Jeff Dimmock” user is highlighted in red.
Now, of course, the Domain Admins group has full control of every other object in Active Directory; however, as attackers, we are interested in how we can abuse ACEs to gain control of a domain admin or a user or group that gets us closer to our target objective. Additionally, the owner of an object has complete control (GenericAll equivalent) of the object, regardless of any explicit deny ACEs.
Common ACEs Abused in Active Directory
- ForceChangePassword: The ability to change the target user’s password without knowing the current value. Abused with Set-DomainUserPassword.
- AddMembers: The ability to add arbitrary users, groups, or computers to the target group. Abused with Add-DomainGroupMember.
- GenericAll: Full object control, including the ability to add other principals to a group, change a user password without knowing its current value, register an SPN with a user object, etc. Abused with Set-DomainUserPassword or Add-DomainGroupMember.
- GenericWrite: The ability to update any non-protected target object parameter value. For example, update the “scriptPath” parameter value on a target user object to cause that user to run your specified executable/commands the next time that user logs on. Abused with Set-DomainObject.
- WriteOwner: The ability to update the owner of the target object. Once the object owner has been changed to a principal the attacker controls, the attacker may manipulate the object any way they see fit. Abused with Set-DomainObjectOwner.
- WriteDACL: The ability to write a new ACE to the target object’s DACL. For example, an attacker may write a new ACE to the target object DACL giving the attacker “full control” of the target object. Abused with Add-NewADObjectAccessControlEntry.
- AllExtendedRights: The ability to perform any action associated with extended Active Directory rights against the object. For example, adding principals to a group and force changing a target user’s password are both examples of extended rights. Abused with Set-DomainUserPassword or Add-DomainGroupMember.
- Self (Self-Membership): Ability to add yourself to a group!
How to Grant GenericAll Permission to a User?
To grant GenericAll permission to a user in Active Directory (AD), follow these steps:
- Open the Active Directory Users and Computers (ADUC) console.
- Navigate to the user account that you want to grant full permission to.
- Right-click on the user account and select “Properties”.
- In the properties window, go to the “Security” tab.
- Click on the “Advanced” button.
- In the “Advanced Security Settings” window, click on the “Add” button.
- In the “Permission Entry” window, click on “Select a principal”, then click “Advanced”, and finally “Find Now”.
- In the “Search” window, find and select the user or group that you want to grant full permission to.
- Click “OK” to close the “Search” window.
- In the “Permission Entry” window, select “This object and all descendant objects” in the “Applies to” dropdown.
- In the “Permissions” section, select “Full control” for the “Allow” permission.
- Click “OK” to close the “Permission Entry” window.
- Click “OK” to close the “Advanced Security Settings” window.
- Click “OK” to close the “Properties” window.
Now, the user or group should have full control permission on the selected user account and all descendant objects in Active Directory.
Note: Use caution when granting this kind of permission and only give it to trusted users or groups.
How to Check if a User Has GenericAll Permissions (using Bloodhound)
- Gather the data using SharpHound and open it in BloodHound.
- Search for the user whose permission you want to check.
- Click on the user, and from the Node Info menu, click on Transitive Object Control.
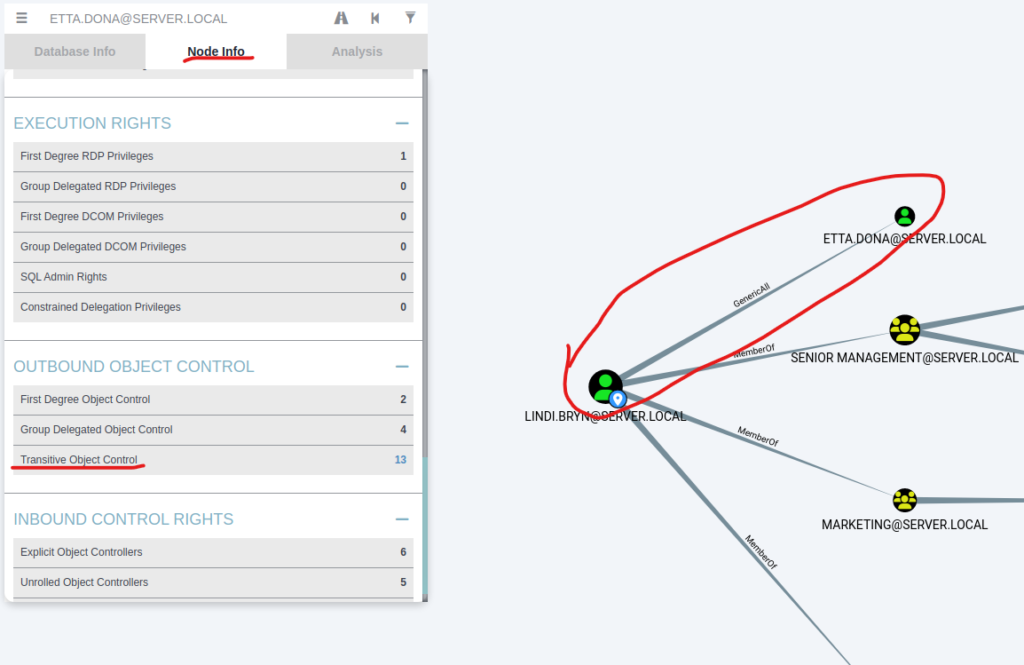
- If the user has GenericAll access over another user, it will be displayed.
In the example below, Lindi.Bryn has GenericAll access over Etta.Dona:
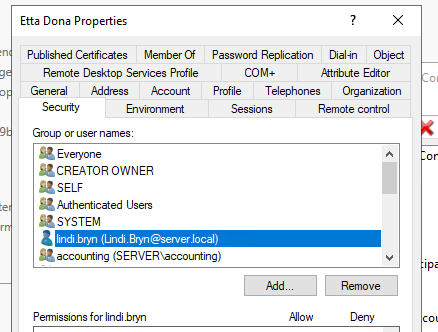
Installing the Active Directory PowerShell Module
The Active Directory module for Windows PowerShell is not installed by default on most systems. It is part of the Remote Server Administration Tools (RSAT) package, which can be installed on Windows client operating systems to manage Windows Server roles and features remotely.
To install RSAT and the Active Directory module, use the following commands:
Add-WindowsFeature RSAT-AD-PowerShell
Or:
Get-WindowsCapability -Name RSAT.ActiveDirectory* -Online | Add-WindowsCapability -Online
Check if You Have GenericAll or Write Permissions on a User
After importing the Active Directory module in PowerShell, use the following command to test if you can modify a user object:
Import-Module ActiveDirectorySet-ADUser -Identity Etta.Dona -Description "Test update"
This command attempts to update the description for the user Etta.Dona. If you don’t have sufficient permissions, the command will fail.
Change the Password of Another User if You Have GenericAll/Write Permission
To change the password of another user in Active Directory (if you have sufficient permissions), use the following PowerShell command:
Set-ADAccountPassword -Identity 'username' -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "NewPassword" -Force
If you want to read about Kerberoasting attack here is the article.
Understanding Kerberoasting: Creation, Exploitation, Impact, and Defense









Comments 1