Introduction
Building an Active Directory HomeLab allows penetration testers and security researchers to test techniques and tools in a controlled environment. AD is a key target in real-world networks, so learning how to identify and exploit AD vulnerabilities is essential. In this guide, we’ll walk through setting up a vulnerable AD environment for practice.
Requirements
Before you begin, make sure you have the following:
- Windows Server: You’ll need Windows Server 2016 or later with the Active Directory Domain Services (AD DS) role installed.
- PowerShell Knowledge: You should be familiar with running scripts in PowerShell, as this process involves executing scripts to create the vulnerable environment.
- Server Manager: Ensure that Active Directory services are running.
Step 1: Installing Active Directory
If you haven’t installed active directory check out this article first.
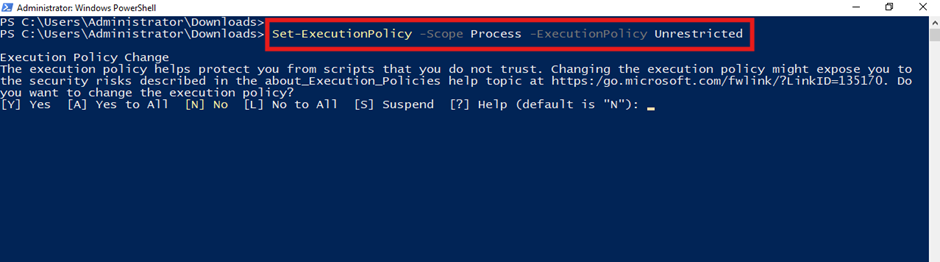
Step 2: Set PowerShell Execution Policy
To run scripts, you need to adjust the PowerShell execution policy. Here’s how:
- Open PowerShell as Administrator.
- Run the following command to temporarily change the execution policy:
Set-ExecutionPolicy -Scope Process -ExecutionPolicy Unrestricted
Typeyto confirm the change. This allows you to execute scripts for the current session without permanently altering your system settings.
Step 3: Downloading and Running the Vulnerable AD Script
The vulnerable Active Directory script is provided by a GitHub repository maintained by wazehell. This script will introduce multiple common AD vulnerabilities.
- In PowerShell, run this command to download and execute the vulnerable AD script
IEX((new-object net.webclient).downloadstring("https://raw.githubusercontent.com/wazehell/vulnerable-AD/master/vulnad.ps1"));
The script will download and create the necessary objects in your AD environment.
Step 4: Running the VulnAD Script
After the script is downloaded, you need to invoke it to create users and simulate vulnerabilities.
- Run the following command to invoke the vulnerable AD script:
Invoke-VulnAD -UsersLimit 100 -DomainName "home.local"Replacehome.localwith your domain name if it’s different.
This will create 100 users and generate a variety of misconfigurations and vulnerabilities in your Active Directory environment.

Check out this video to understand the process.
Step 5: Vulnerabilities Created by the Script
The script will automatically introduce the following vulnerabilities:
- Abusing ACLs/ACEs: Misconfigurations in access control lists (ACLs) and access control entries (ACEs) allow privilege escalation and lateral movement.
- Kerberoasting: Extract service tickets for offline cracking of service account passwords.
- AS-REP Roasting: Exploit accounts that don’t require pre-authentication, allowing password hash extraction.
- DnsAdmins Abuse: Members of the DnsAdmins group can execute code as SYSTEM.
- Password in Object Descriptions: Weak passwords are stored in object descriptions, making them accessible to attackers.
- User Objects with Default Passwords: Users with the default password “Changeme123!” are created, making brute-force attacks easier.
- Password Spraying: Allows for testing common passwords across many accounts.
- DCSync Attack: Extract password hashes from the domain controller using replication privileges.
- Silver Ticket & Golden Ticket: Abuse Kerberos tickets for persistence and lateral movement.
- Pass-the-Hash & Pass-the-Ticket: Use password hashes or Kerberos tickets to authenticate without knowing plaintext passwords.
- SMB Signing Disabled: SMB signing is disabled by default, allowing for man-in-the-middle attacks.
Conclusion
Setting up a vulnerable Active Directory homelab is an excellent way to learn about the inner workings of AD security and the various attack vectors. By following this guide, you’ll be able to test common AD attacks like Kerberoasting, DCSync, and Pass-the-Hash. This hands-on experience will significantly enhance your penetration testing skills.
Disclaimer: This blog is for educational purposes only, promoting awareness of ethical hacking and cybersecurity to help readers protect against cyber threats. All content is based on lawful experiments on our own systems. No illegal activities are endorsed. Users agree to apply the information responsibly and legally. The blog and author are not liable for any misuse. By using this blog, you agree to use all knowledge ethically and legally. [Read full disclaimer].