What is BloodHound?
BloodHound is a powerful open-source tool that helps with penetration testing in Active Directory environments. It allows security professionals to see and understand the relationships and permissions within Active Directory using an easy-to-navigate graphical interface. By visualizing these connections, BloodHound makes it simpler to spot potential vulnerabilities and assess the overall security of an organization.
What is SharpHound?
SharpHound is a data collection tool for bloodhound it uses Lightweight Directory Access Protocol (LDAP) to gather information about users, groups and services and their respective permission and permission between different AD objects.
Installing and running BloodHound in Linux.
Step 1 : Install BloodHound – Open your terminal and install Bloodhound using the following command:
sudo apt install bloodhound
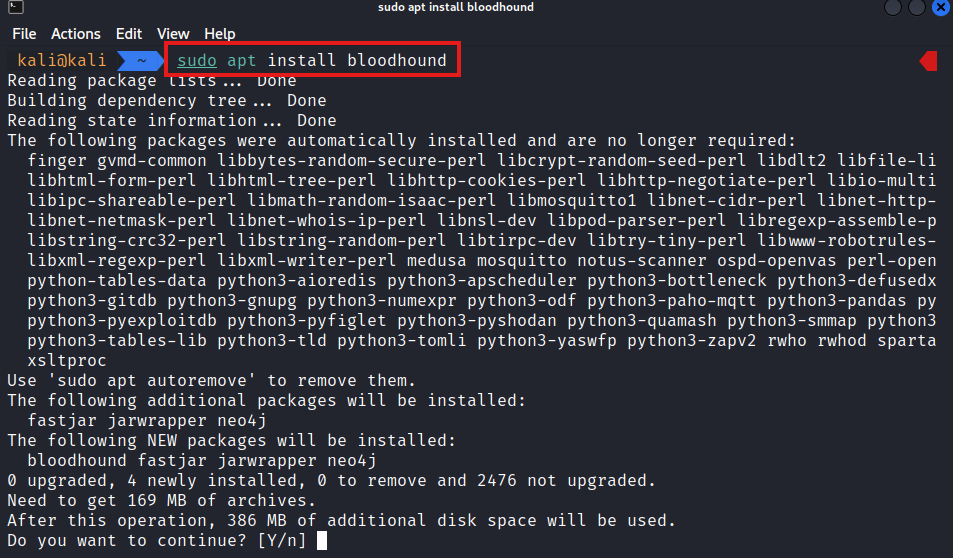
Step 2 : Start Neo4j Service – Once the installation is complete, you need to start the Neo4j service. In your terminal, run:
sudo neo4j console

Step 3 : Access the Neo4j Interface
- Open your browser and navigate to: http://localhost:7474/
- Use the default credentials to log in:
- Username:
neo4j - Password:
neo4j
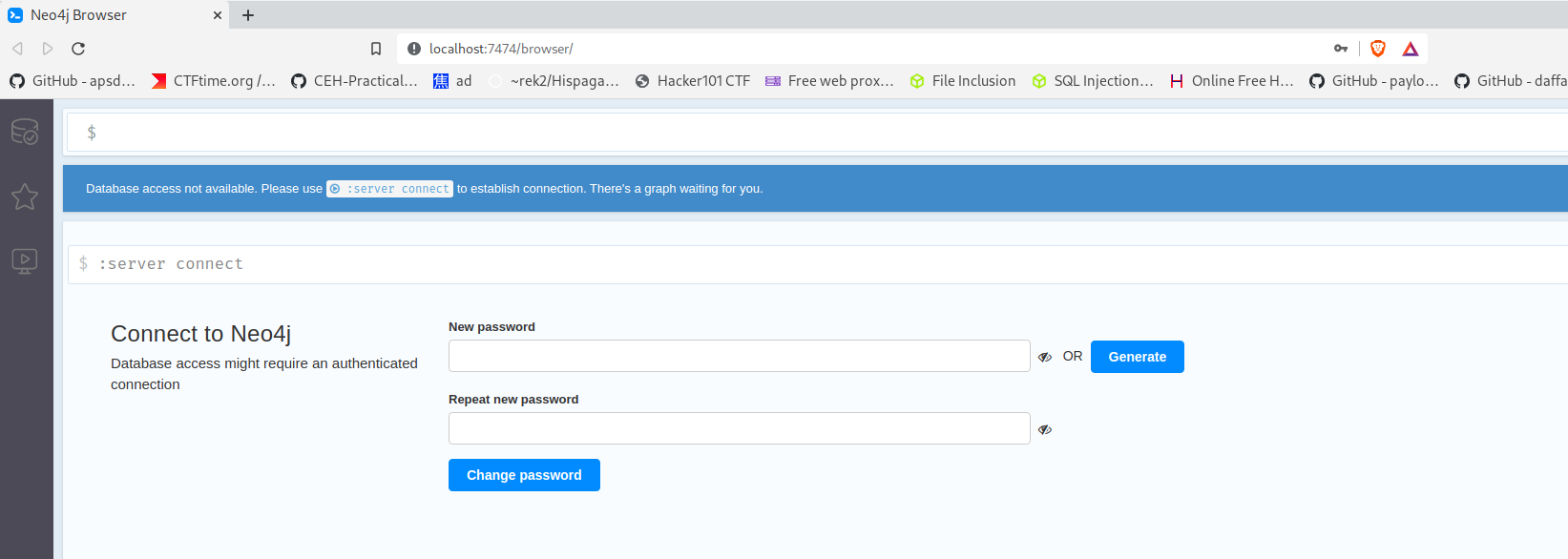
- Username:
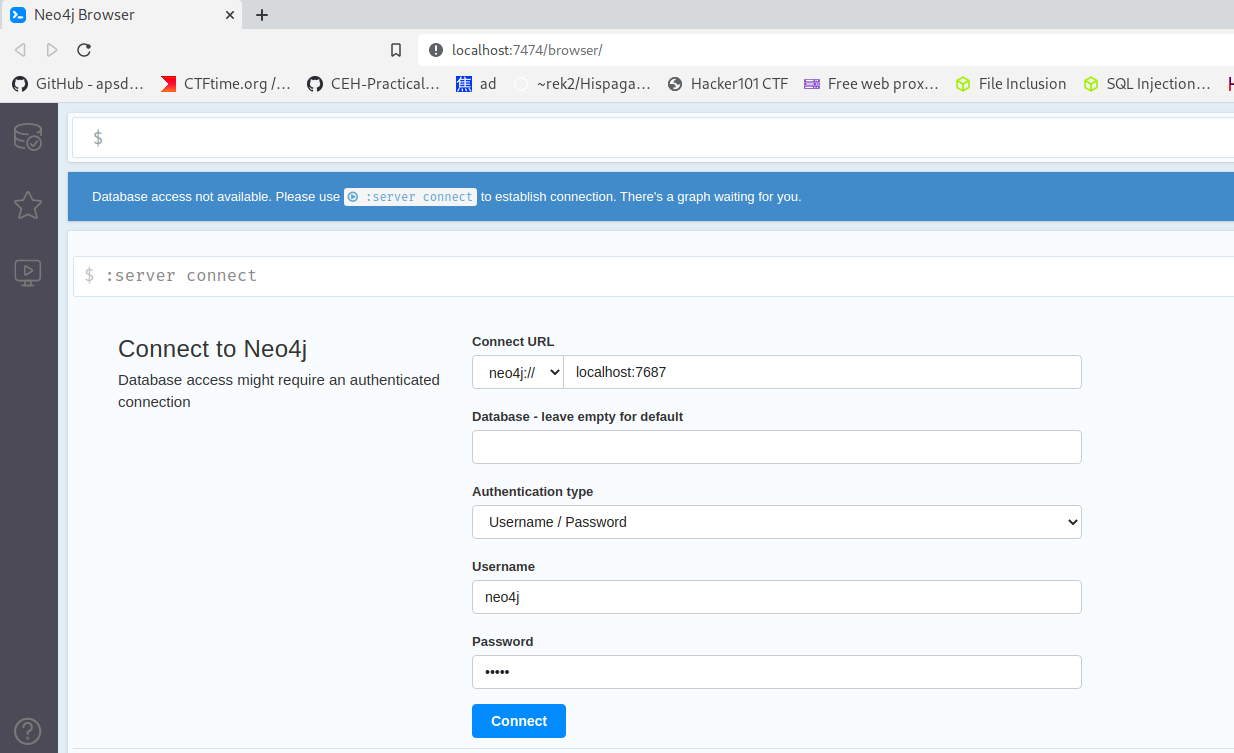
Step 4 : Update Your Password – You will be prompted to change the default password. Make sure to set a secure, memorable password, as you’ll use it to log into Bloodhound.
Step 5 : Run BloodHound – To launch Bloodhound, open a new terminal window and execute:
bloodhound

Step 6 : Login to Bloodhound – Login in bloodhound using the updated password.
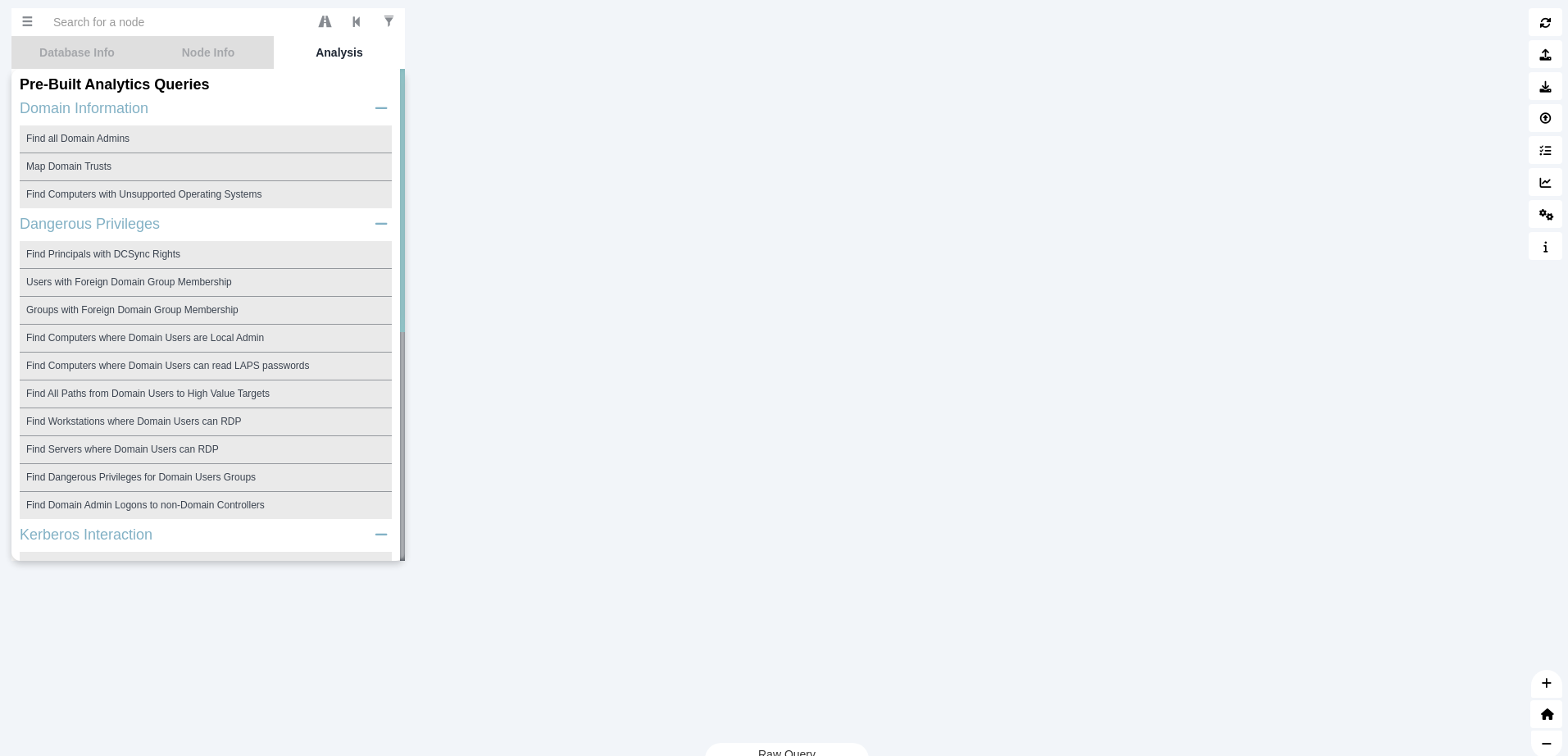
Collecting Data Using SharpHound for BloodHound Analysis
Bloodhound uses data collected by SharpHound to analyze and visualize Active Directory environments. Follow the steps below based on your access type (GUI or CLI).
Download SharpHound
You can download SharpHound from the official BloodHound GitHub repository: Download SharpHound
Data Collection Methods
1. Using GUI Access
If you have GUI access to a machine connected to the Active Directory environment:
- Locate and double-click SharpHound.exe.
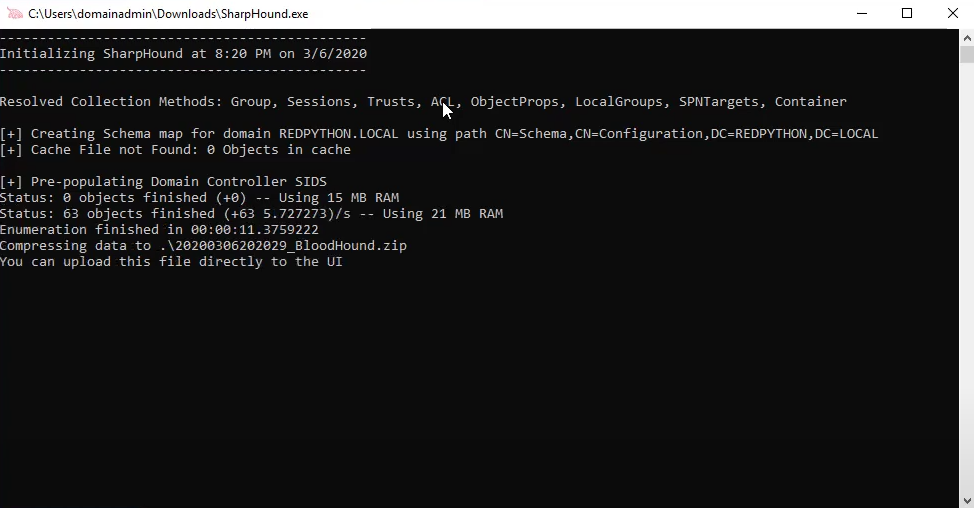
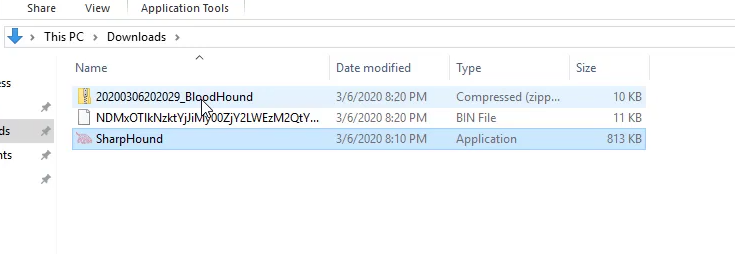
- The collected data will be automatically stored in the same directory as SharpHound.exe.
2. Using CLI Access (e.g., SSH)
NOTE: Make sure that SharpHound.ps1 is on same directory.
If you are accessing the machine using SSH or a command-line interface:
- Open PowerShell:
powershell
- Set the Execution Policy:
Set-ExecutionPolicy -ExecutionPolicy Unrestricted
- Load SharpHound PowerShell Script:
. .\SharpHound.ps1
- Run SharpHound to Collect Data: Replace home.local with your domain name.
Invoke-BloodHound -CollectionMethod All -Domain CONTROLLER.local -ZipFileName loot.zip
Collecting Data with Evil-WinRM or PowerShell for Linux
If you are using Evil-WinRM or PowerShell on a Linux system:
- Set the Execution Policy:
Set-ExecutionPolicy -ExecutionPolicy Unrestricted
- Load SharpHound PowerShell Script:
. .\SharpHound.ps1
- Run SharpHound with Credentials: Replace <UserName>, <Password>, and <PathToFile> with your details.Invoke-BloodHound -CollectionMethod All -LdapUsername <UserName> -LdapPassword <Password> -OutputDirectory <PathToFile>
OR
. .\SharpHound.ps1
Invoke-BloodHound -CollectionMethod All –LdapUsername <UserName> –LdapPassword <Password> –OutputDirectory <PathToFile
Visualizing data collected by SharpHound on BloodHound.
Step 1. Upload the zip file created by SharpHound on BloodHound tool.

Wait until the upload is completed.
You can now see and understand the relationships and permissions within Active Directory using an easy-to-navigate graphical interface.
Complete Video Walkthrough:
Read similar articles :
How to perform Golden Ticket Attack in Active Directory in 2025?
Disclaimer: This blog is for educational purposes only, promoting awareness of ethical hacking and cybersecurity to help readers protect against cyber threats. All content is based on lawful experiments on our own systems. No illegal activities are endorsed. Users agree to apply the information responsibly and legally. The blog and author are not liable for any misuse. By using this blog, you agree to use all knowledge ethically and legally. [Read full disclaimer].