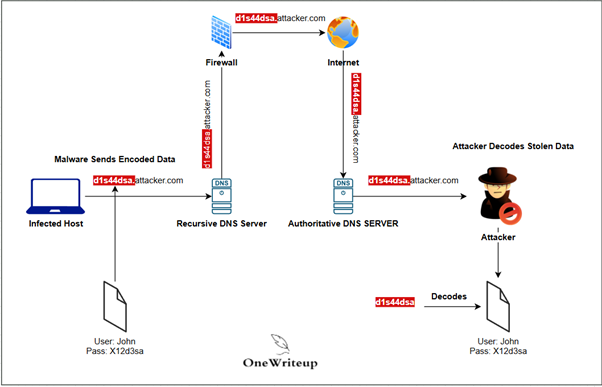
DNS-based data exfiltration is a stealthy cyberattack technique in which an attacker funnels sensitive data out of a network by cleverly disguising it within ordinary DNS (Domain Name System) requests and responses. Since DNS is a critical backbone of internet communication—responsible for translating website names into IP addresses—its traffic is almost never blocked, making it an attractive channel for attackers to exploit.
How DNS Data Exfiltration Works
DNS exfiltration is like stealing the parts of a PC one by one and secretly putting the computer back together at your own house after you’ve collected every piece. Instead of carrying the whole computer out the door, you grab a CPU here, a memory stick there, maybe a graphics card next—each trip looks harmless. But in the end, you own the entire working computer without ever carrying out something big and obvious.
Here’s how it looks in the world of cyberattacks:
- Attacker Prepares the Trap:
The attacker buys a special domain—call it Attacker.com—and sets up their own DNS server to watch for incoming queries. - Malware Breaks Data into Chunks:
On a compromised computer inside your company, the malware wants to steal a key file—let’s say it holds client data. But it doesn’t send the whole file at once. Instead, it breaks the file into tiny parts, like someone stealing one hard drive, then the RAM, then the CPU. - Sending Each Chunk:
Each small bit of data is encoded (think: turning the components into code words) and hidden in a DNS request, like d1s44dsa.attacker.com. Each query only contains one small fragment. - Passing Security Unnoticed:
The company DNS server sees thousands of outgoing DNS queries every hour, so these sneaky requests blend right in—nothing seems suspicious about asking “What’s the address for d1s44dsa.attacker.com?” or “fra12xaq2.attacker.com?” - The Attacker Reassembles the Parts:
Their DNS server collects each incoming chunk. Once every part is received, the attacker puts them all back together—reconstructing your sensitive data piece by piece, just as someone could reassemble a stolen PC in their living room.
In short:
DNS exfiltration lets attackers smuggle out valuable data one tiny piece at a time, using the ordinary flow of DNS requests that most organizations trust and rarely block. By the time you realize what’s happened, the digital ”Sensitive Data” has already been exfiltrated somewhere else, right under your nose.
Dns Based Data Exfiltration Using Burp Collaborator Client
Overview
The script exfil_hardened_v3.1.ps1 takes sensitive data from an internal variable, converts it into a hex format, breaks it into DNS-compliant chunks, and sends those chunks as DNS queries to a domain controlled by the attacker (here represented as a Burp Collaborator URL). This allows data to be smuggled out through DNS traffic, which often bypasses traditional security controls.
NOTE: Burp Collaborator Feature is available only on the Pro version of BurpSuite
These are some alternative websites which can capture DNS requests.
Detailed Explanation
1. Configuration
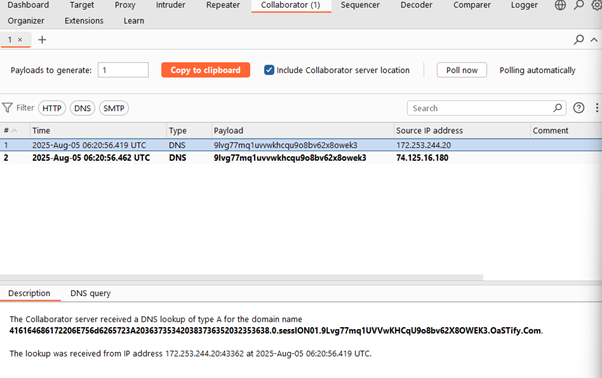
- This is the Burp Collaborator URL: (9lvg77mq1uvvwkhcqu9o8bv62x8owek3.oastify.com) where the exfiltrated data is sent.
- A unique session identifier (session01) used to tag DNS queries from this specific exfiltration session.
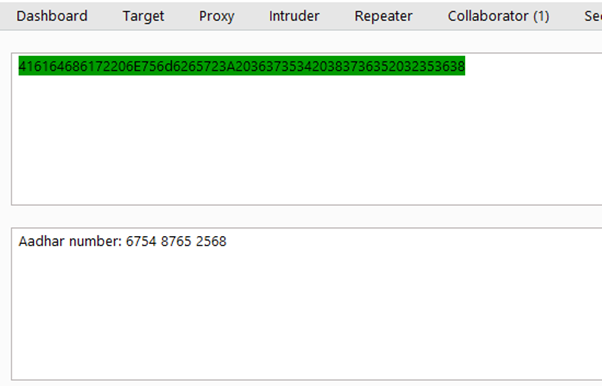
2. Sensitive Data Being Exfiltrated
- In this case, an example string with an “Aadhar number: 6754 8765 2568”.
3. Encoding the Payload
- The payload string is converted to bytes using UTF-8 encoding.
- Each byte is converted to a two-character lowercase hexadecimal representation (x2), resulting in a hex string.
- This hex string serves as a safe way to represent potentially sensitive binary or text data within DNS-compatible characters.
- Status is output with Write-Host for success or failure in this step.
4. Chunking the Hex String
- DNS labels (subdomains) have length limits (max 63 characters).
- The script splits the hex string into smaller chunks of 60 characters to comply with DNS label length restrictions.
- These chunks are saved in an array
- Outputs the total number of chunks split.
5. Sending Data Over DNS
- The script loops over each chunk.
- For each chunk, it prepares a DNS query in the form:
- <chunk>.<chunk_number>.<sessionID>.<collaboratorURL>
- E.g., something like: 4f6a…3c4a.0.session01.9lvg77mq1uvvwkhcqu9o8bv62x8owek3.oastify.com
- This query embedding allows the attacker’s DNS server (Burp Suite Collaborator) to receive and reconstruct the exfiltrated data by parsing the subdomain parts.
- It uses the Resolve-DnsName cmdlet to send the DNS A record query silently, ignoring errors.
- A small delay of 200 milliseconds between queries to evade detection from sudden traffic spikes.
- Outputs the progress of each chunk sent.
6. Completion
After all chunks are sent, it prints a completion message.
Script Summary
This script covertly sends sensitive internal data by encoding it into DNS query subdomains and routing those queries to an attacker-controlled DNS server. The chunking handles DNS length limits, and the DNS traffic blends into normal network behavior, making detection challenging without thorough monitoring of DNS logs.
DNS Tunneling: Command & Control
More advanced attacks use what’s known as DNS tunneling. Here, attackers not only send data out, but also receive commands using DNS response packets, essentially creating a two-way covert channel. Tools like iodine and dnscat2 can set up these tunnels, enabling prolonged remote control over compromised systems without detection.
Why Is Detection Difficult?
Detecting DNS exfiltration is challenging because:
- DNS traffic is almost universally permitted and essential for business operations.
- Malicious queries are disguised as legitimate requests, and low-volume exfiltration evades typical traffic monitoring.
- Attackers often use rotating domains or obscure record types (like TXT or CNAME) to bypass basic filtering.
How Can Organizations Protect Themselves?
To counteract these attacks, organizations should:
- Analyze DNS logs for unusual activity, such as abnormally long queries, high volumes of external domain lookups, or records with excessive entropy.
- Restrict DNS resolution so only approved internal servers can handle DNS queries, blocking direct outbound connections to suspicious or unknown DNS servers.
- Leverage machine learning and analytics to identify subtle deviations in DNS usage, as human analysts can’t keep up with the scale and sophistication of modern attacks.
- Implement threat intelligence and Response Policy Zones (RPZs) to dynamically block traffic to known bad domains, although attackers may bypass these with fast-changing domain names.
- Utilize advanced DNS security platforms that scan, log, and inspect DNS traffic in real time, catching exfiltration before data leaves the perimeter.
Final Thoughts
DNS-based data exfiltration is a testament to how attackers can turn essential internet protocols into tools of espionage. Because DNS is fundamental to every network, safeguarding it with vigilant monitoring, modern security tools, and strict access policies is not just best practice—it’s a necessity for any organization serious about protecting its information.
Disclaimer: This blog is for educational purposes only, promoting awareness of ethical hacking and cybersecurity to help readers protect against cyber threats. All content is based on lawful experiments on our own systems. No illegal activities are endorsed. Users agree to apply the information responsibly and legally. The blog and author are not liable for any misuse. By using this blog, you agree to use all knowledge ethically and legally. [Read full disclaimer].
Disclaimer: This blog is for educational purposes only, promoting awareness of ethical hacking and cybersecurity to help readers protect against cyber threats. All content is based on lawful experiments on our own systems. No illegal activities are endorsed. Users agree to apply the information responsibly and legally. The blog and author are not liable for any misuse. By using this blog, you agree to use all knowledge ethically and legally. [Read full disclaimer].