Most Effective Tools for Subdomian Enumeration Are:
- Amass – A powerful tool for network mapping and asset discovery, supporting both passive and active enumeration.
- Sublist3r – An OSINT-based Python tool that integrates with multiple search engines and services to find subdomains.
- Ffuf (Fast Web Fuzzer) – A fast and flexible web fuzzer used for brute-forcing subdomains and virtual host discovery.
- DnsRecon – A DNS enumeration tool capable of conducting DNS record checks and brute-force attacks for comprehensive reconnaissance.
- WhoisXML Subdomain Lookup – Offers accurate data points including subdomains, with API integration and batch feed capabilities.
- Criminal IP – Focuses on domain scoring and threat hunting, providing insights like communication history and technical stack details.
- DNSDumpster – Visualizes subdomains using SSL certificate logs and web archives, making it a popular choice for pentesters.
- MassDNS – A high-performance DNS stub resolver that supports efficient bulk lookups, ideal for large-scale engagements.
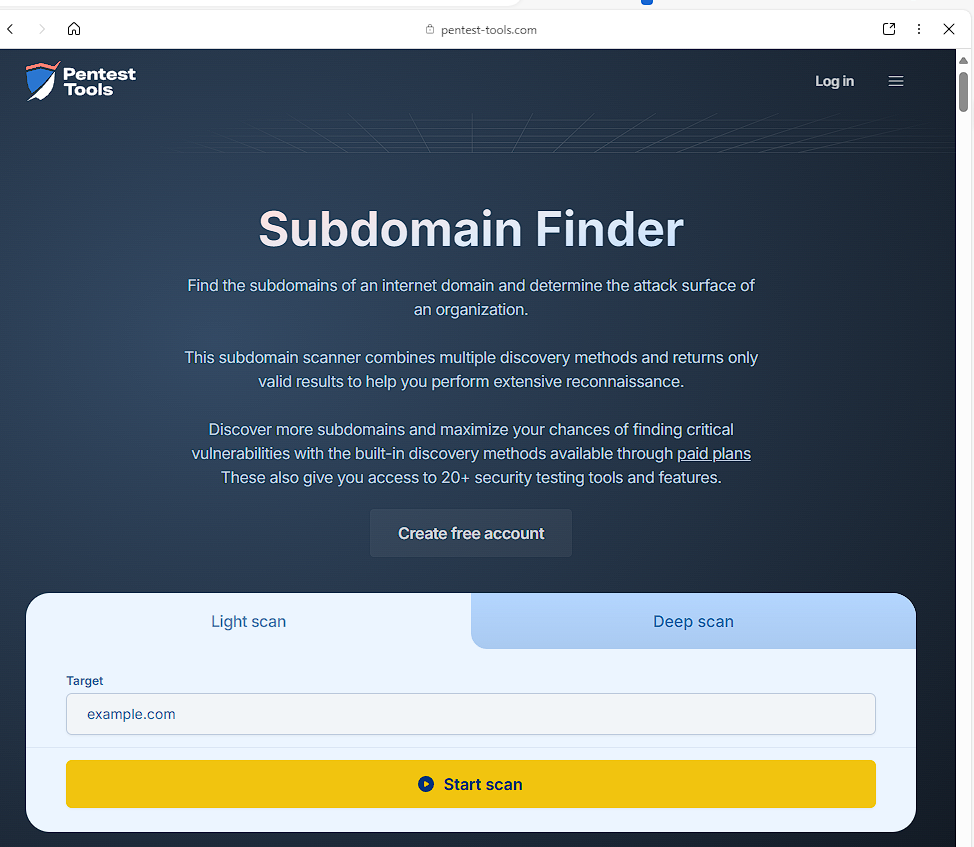
- Pentest-Tools Subdomain Finder – Combines multiple discovery techniques into a single platform for efficient vulnerability assessments.
What is Subdomain Enumeration?
Subdomain enumeration is the process of identifying subdomains for a given domain. In cybersecurity, this step is essential for penetration testing and vulnerability assessments because it allows ethical hackers and security professionals to discover potential entry points that may be overlooked.
Types of Subdomain Enumeration Techniques
Subdomain identification techniques can generally be divided into passive and active methods:
Passive Subdomain Enumeration
Passive subdomain enumeration involves collecting subdomain information through third-party sources without directly engaging the target infrastructure. This method is less likely to trigger security alarms compared to active methods. Techniques include Google Dorking, ASN Lookups, and using services like VirusTotal and DNSDumpster.
Active Subdomain Enumeration
Active subdomain enumeration involves engaging directly with the target infrastructure, often creating noticeable traffic that could be detected by firewalls or IDSs. Techniques include brute-forcing subdomains using tools like ffuf and Amass.
Top Passive Subdomain Enumeration Techniques
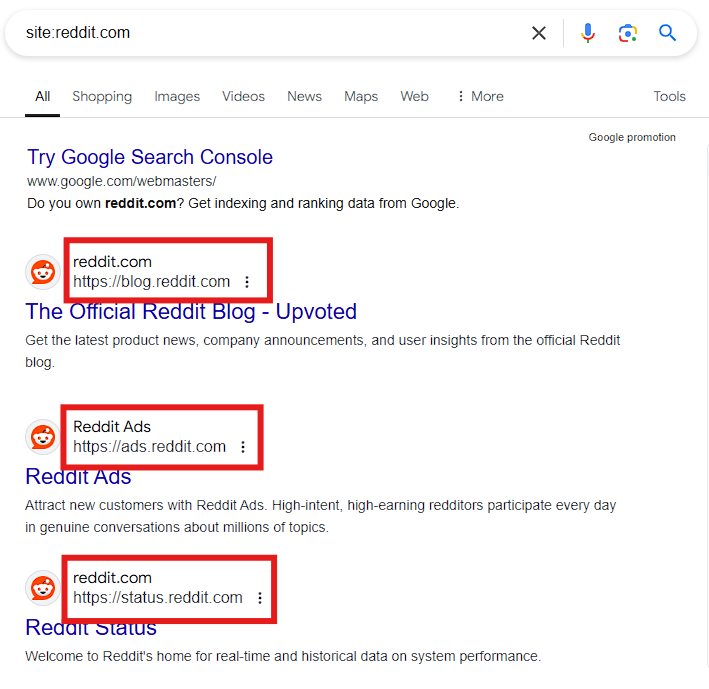
Google Dorking
Using advanced search operators such as site: to locate all indexed subdomains of a target domain. For example, searching site:example.com will reveal all subdomains indexed by Google.
Autonomous System Number (ASN) Lookups
ASNs serve as unique identifiers for IP prefixes managed by network operators. Tools like asn.cymru.com and bgp.he.net can help find related ASNs, which can then be further enumerated using Amass.

Subject Alternative Name (SAN) Certificates
A single SAN certificate can cover multiple subdomains. Scripts like san_subdomain_enum.py can help extract these subdomains. https://knowledge.digicert.com/solution/what-is-san-certificate
Content Security Policy (CSP) Headers
CSP headers specify where resources can be loaded on a web page. Extracting CSP headers using commands like curl --head -s -L | grep -iE "Content-Security-Policy|CSP" can help identify subdomains.
Third-Party Services
Third-party services like VirusTotal, DNSDumpster, and Findomain aggregate DNS data from various sources and provide extensive details about subdomains, including historical DNS data and visual maps.
Certificate Transparency (CT) Logs
CT logs, like crt.sh or censys.io, store SSL/TLS certificates issued by Certificate Authorities (CAs), making them searchable to find subdomains associated with a domain name.
Internet Archives
Tools like Gauplus and Unfurl use archived internet data to identify subdomains and endpoints that might otherwise be missed through other methods.

Top Active Subdomain Enumeration Techniques
Amass
Amass is a comprehensive network mapping and asset discovery tool that supports both passive and active modes. It uses brute-forcing, reverse DNS sweeping, and other methods for subdomain enumeration. For passive enumeration, the command amass enum --passive -d example.com is used.

Sublist3r
An open-source intelligence (OSINT)-powered Python tool used for discovering subdomains. Sublist3r integrates with multiple search engines and services, making it a useful means of discovering subdomains.

Ffuf (Fast Web Fuzzer)
As a quick web fuzzer written in Go, Ffuf supports brute-forcing subdomains via wordlists, virtual host discovery, and GET/POST parameter fuzzing.

DnsRecon
DnsRecon is a powerful DNS enumeration and brute-force attack tool that checks DNS records and performs PTR record lookups to complete in-depth reconnaissance.

Best Subdomain Enumeration Tools Available Now
WhoisXML Subdomain Lookup
Ideal for developers, providing accurate data points, including subdomains and timestamps. This service features GUI tools, API integration, and batch feeds.

Criminal IP
Focuses on domain scoring and threat hunting to provide security insights such as communication history and technical stack information.

DNSDumpster
Visualizes subdomains using data sourced from SSL certificate logs and web archives.

MassDNS
MassDNS is a high-performance DNS stub resolver designed to support bulk lookups efficiently, making it ideal for handling large numbers of domain names.

Pentest-Tools Subdomain Finder
Combines multiple discovery techniques and provides an efficient tool for vulnerability assessments or broad engagements.
Advantages of Subdomain Finder Tools
1. Enhancing Security
Uncovering hidden subdomains helps safeguard against potential attacks by protecting weak or forgotten endpoints.
2. Comprehensive Reconnaissance
Exhaustive mapping of domains and subdomains is indispensable when conducting vulnerability analyses.
3. Time-Saving Automation
Automating subdomain discovery saves valuable time and resources.
4. Enhancing Incident Response
Early identification of unapproved subdomains can facilitate effective incident response strategies.
5. Brand Protection
Recognizing potentially misused subdomains will help safeguard both brand reputation and prevent their misuse in the future.
Best Practices for Effective Subdomain Enumeration
- Regular Monitoring and Scanning: Regular scans ensure that new subdomains are promptly identified and secured.
- Combining Multiple Tools and Techniques: Using both passive and active techniques in tandem offers a more comprehensive approach.
- Understanding Legal Implications: Always ensure that subdomain enumeration is performed ethically and within legal boundaries.
- Using Automation with Caution: While automation saves time, it should be monitored to avoid detection and unintended disruptions.
Frequently Asked Questions (FAQs)
What is Subdomain Enumeration?
Subdomain enumeration is the process of discovering subdomains associated with a main domain to identify potential entry points and vulnerabilities.
Why is Subdomain Enumeration Important?
It is essential for uncovering hidden vulnerabilities, improving incident response, and ensuring compliance with security standards.
What are Passive Subdomain Enumeration Techniques?
These involve using third-party data and services without engaging directly with the target infrastructure, such as Google Dorking and ASN lookups.
What are Active Subdomain Enumeration Techniques?
Active techniques directly interact with the target domain’s infrastructure, often using tools like Amass and Ffuf.
What Tools Are Best for Subdomain Enumeration?
Top tools include Amass, Sublist3r, Ffuf, MassDNS, and WhoisXML Subdomain Lookup.
How Can I Automate Subdomain Enumeration?
Automation can be done using scripts and integrating tools like Amass into CI/CD pipelines for continuous monitoring.
Conclusion
Subdomain enumeration is an essential practice for cybersecurity professionals and ethical hackers alike. Utilizing passive and active enumeration techniques with appropriate tools, as well as following the benefits and best practices discussed herein, can greatly enhance security assessments. From using simple Google Dorks to advanced tools such as Amass, Sublist3r, and ffuf, mastering these techniques ensures robust protection against potential threats. Stay proactive by regularly monitoring and enumerating subdomains to boost domain security posture and protect critical assets from malicious actors.
Disclaimer: This blog is for educational purposes only, promoting awareness of ethical hacking and cybersecurity to help readers protect against cyber threats. All content is based on lawful experiments on our own systems. No illegal activities are endorsed. Users agree to apply the information responsibly and legally. The blog and author are not liable for any misuse. By using this blog, you agree to use all knowledge ethically and legally. [Read full disclaimer].