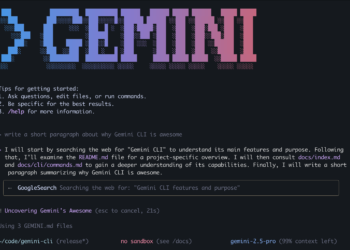
Introduction
QR codes have become a significant part of our daily lives, being used for quick information access, payments, authentication, and more. However, like any technology, QR codes are not without their vulnerabilities. In this case study, we will explore a security vulnerability found in QR code scanners and image-to-text scanners like Google Lens, QR based logins and others. This vulnerability, inspired by a HackerOne report from the user “mrzheev,” involved injecting an XSS (Cross-Site Scripting) payload into a QR code that triggered an XSS alert on a vulnerable QR scanner.
This guide is meant to provide a deeper understanding of how such vulnerabilities can be exploited and how to protect against them. Let’s dive into the step-by-step process.
Step 1: Creating a QR Code Payload
To exploit a QR code vulnerability, the first step involves creating a QR code embedded with an XSS payload. When scanned by a vulnerable QR code scanner, the payload triggers an XSS alert.
There are two primary methods for generating a QR code payload:
Method 1: Using Online QR Code Generators
There are several online tools to create QR codes. In this example, we will use “QR Code Generator | Forever Free QR Codes” (the-qrcode-generator.com). This website allows users to generate QR codes for free. Here’s how to do it:
- Visit the website: the-qrcode-generator.com.
- Enter the payload for the XSS attack in the URL section. For example:
javascript:alert(document.domain);. - Generate the QR code by clicking the “Generate” button.
- Save or download the generated QR code to your computer.

This QR code now contains a script that will execute when scanned by a vulnerable scanner.
Method 2: Using Python to Generate QR Codes
For those more comfortable with programming, generating a QR code using Python is an effective approach. The qrcode library in Python provides the tools to create custom QR codes with the desired payload:
import qrcode# Create a new QR Code instance
qr = qrcode.QRCode(version=1, error_correction=qrcode.constants.ERROR_CORRECT_L, box_size=10, border=4)
# Add the XSS payload to the QR code
qr.add_data("javascript:alert(document.domain);")
# Compile the data into a QR code
qr.make(fit=True)
# Create an image of the QR code
img = qr.make_image(fill_color="black", back_color="white")
# Save the image to a file
img.save("xss_qrcode.png")
This script will create a QR code (xss_qrcode.png) that triggers a JavaScript alert with the domain of the document when scanned by a vulnerable QR code scanner.
Outcome: Vulnerable QR Code Generated
By following either of these methods, you now have a QR code that, when scanned by a vulnerable scanner, will attempt to execute the embedded XSS payload.
Step 2: Testing the QR Code on Different Scanners
With the QR code payload created, the next step is testing it on various QR code scanners. Some scanners are designed to be more secure, while others might be vulnerable to such XSS attacks.
Testing on Brave Browser’s QR Scanner
- Open the Brave Browser and access its QR code scanner feature.

- Scan the generated QR code (
xss_qrcode.png) from the previous step. - Observe the result: If the scanner is vulnerable, you should see a JavaScript alert popping up, displaying the
document.domain.

This proof of concept demonstrates that certain QR code scanners do not sanitize input properly and can be exploited for XSS. Note: Brave Browser and many other services have since patched this vulnerability, ensuring users’ safety from such attacks.
Testing on Other Vulnerable Platforms
You can test the QR code on other platforms, such as:
- QR-based login pages: Some websites use QR codes for authentication purposes. If these systems do not sanitize the input correctly, the same XSS payload could be executed.
- Image-to-text readers: Tools like Google Lens, which translate text from images, might also interpret a QR code with a payload if they do not properly sanitize inputs.
- QR-code Scanners
- Barcode Reader
Outcome: Understanding the Vulnerability
By testing the QR code on different scanners, it is clear that input sanitization is critical. Vulnerable scanners could expose users to malicious XSS attacks, causing significant security risks.
Step 3: Understanding the Implications and Patch Measures
Implications of QR Code Vulnerabilities
When QR scanners or image-to-text readers do not sanitize input correctly, it can lead to various security threats, such as:
- Cross-Site Scripting (XSS): As demonstrated, XSS attacks can allow attackers to execute scripts that can steal user data or hijack sessions.
- Phishing Attacks: QR codes could direct users to malicious websites that mimic legitimate ones.
- Data Theft: Unsanitized QR codes could also be used to extract sensitive information from a user’s device.
Measures Taken to Patch the Vulnerability
In the case of Brave Browser, the development team addressed the vulnerability by implementing stricter input sanitization measures. These measures include:
- URL validation: Ensuring that only valid URLs are processed and executed.
- JavaScript blocking: Blocking any JavaScript execution that comes from QR code scans.
- Regular Security Audits: Implementing regular audits and updates to the scanner’s codebase to prevent future vulnerabilities.
Best Practices for Developers and Users
To avoid such vulnerabilities:
- Sanitize all inputs: Always ensure that any input coming from an external source, such as QR code scans, is thoroughly sanitized.
- Educate Users: Users should be educated on the risks associated with scanning unknown QR codes and the importance of using trusted scanners.
- Regular Updates: Developers should keep software up-to-date with the latest security patches.
Think Outside The Box
This is just one example of how changing your methodology slightly can help you achieve XSS. Don’t limit yourself to placing XSS scripts in form fields—think outside the box! Attack vectors like QR codes, image-to-text readers, or other non-traditional inputs can also be vulnerable, and creative thinking is often the key to uncovering them. By exploring less conventional methods, you might find security gaps that others have overlooked.
If you enjoyed this tutorial and found it useful, be sure to check out our other posts for more insights and creative approaches to ethical hacking!
Conclusion
This case study highlights the importance of understanding the potential vulnerabilities in commonly used technologies like QR code scanners. While this example focused on XSS attacks via QR codes, the broader lesson is the critical need for input sanitization and security awareness. The vulnerability discussed has been patched, but the principles of ethical hacking and security testing remain ever-relevant.
Disclaimer: This blog is for educational purposes only, promoting awareness of ethical hacking and cybersecurity to help readers protect against cyber threats. All content is based on lawful experiments on our own systems. No illegal activities are endorsed. Users agree to apply the information responsibly and legally. The blog and author are not liable for any misuse. By using this blog, you agree to use all knowledge ethically and legally. [Read full disclaimer].