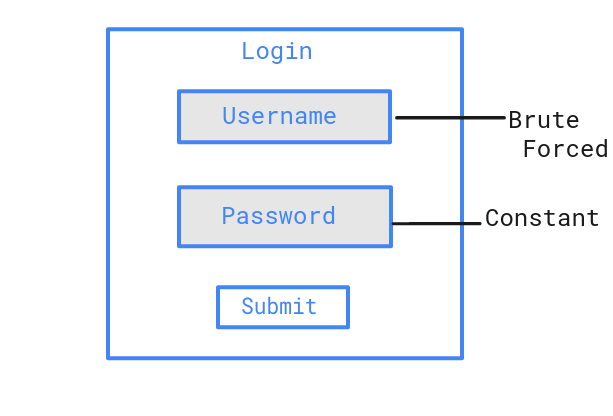
Password Spraying Attack in Active Directory.
Password Spraying attack is a type of brute-force attack in Active Directory in which the attacker uses a same password to brute-force logins based on list of usernames.
For example, an attacker will use one password (say, Admin@123) against many different accounts on the application to avoid account lockouts that would normally occur when brute forcing a single account with many passwords.
Requirements for Password Spraying Attack.
The Attacker need a list of valid usernames of Active Directory Environment to perform the Password Spraying Attack.
The Attacker can get this list by various methods like Publicly Available Information, Data Breaches, Phishing Campaigns, OSINT Tools, DNS Enumeration, Brute Force Username Guessing, Network Sniffing, Collaboration Platforms, Service-Specific APIs, Reconnaissance Tools, Forums and Community Sites, Guessing Based on Context, Compromised Devices, Workplace Insider.
The most common way is companies having emails as account usernames, such as [email protected].
Tool used to perform Password Spraying Attack.
Kerbrute : A tool to quickly brute-force and enumerate valid Active Directory accounts through Kerberos Pre-Authentication.
Kerbrute has four main commands:
- bruteuser – Brute-force a single user’s password from a wordlist
- bruteforce – Read username:password combos from a file or stdin and test them
- passwordspray – Test a single password against a list of users
- userenum – Enumerate valid domain usernames via Kerberos
Syntax:
./kerbrute_linux_amd64 passwordspray -d 'server.local' ~/Downloads/usernames.txt ncc1701This command instructs the Kerbrute tool to perform a password spraying attack against the domain server.local, using the usernames from usernames.txt, attempting the password ncc1701 for each user listed in that file.
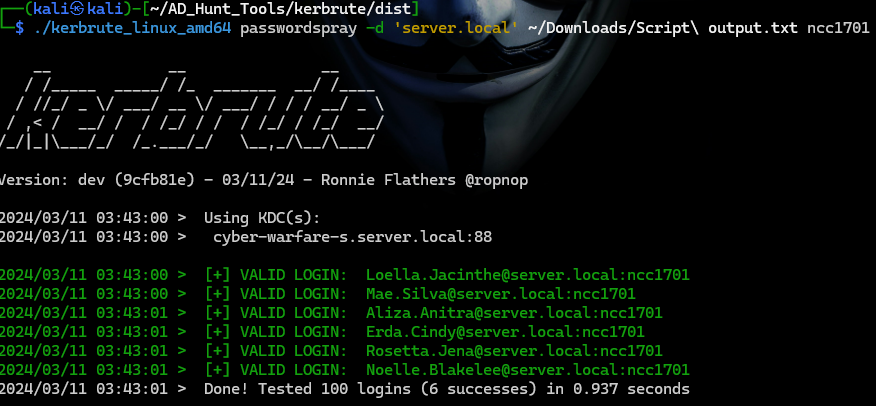
Here are all the users who have ncc1701 password.
How SOC team can detect Password Spraying Attack?
The Password Spraying Attack can be detected by a Sudden Spike in Failed Logins.
Kerberos Failed logins : ID 4768, 4769, 4771
Windows Failed logins: ID 4625, ID 4776
How to Mitigate Password Spraying Attack?
- Implement strong password policies, complexity, length, retention, and uniqueness.
- Deploy and widely adopt MFA and user education.
- Enhance monitoring and anomaly detection, log analysis and alerts, and incident response.
- Educate users on secure password practices, security and phishing awareness training, and reporting mechanisms.
Read Similar Articles:
What is As-Rep Roasting attack in Active Directory and How does it work?
Disclaimer: This blog is for educational purposes only, promoting awareness of ethical hacking and cybersecurity to help readers protect against cyber threats. All content is based on lawful experiments on our own systems. No illegal activities are endorsed. Users agree to apply the information responsibly and legally. The blog and author are not liable for any misuse. By using this blog, you agree to use all knowledge ethically and legally. [Read full disclaimer].